A Systematic Review on Recent Trends, Challenges, Privacy and Security Issues of Underwater Internet of Things
- PMID: 34960366
- PMCID: PMC8706400
- DOI: 10.3390/s21248262
A Systematic Review on Recent Trends, Challenges, Privacy and Security Issues of Underwater Internet of Things
Abstract
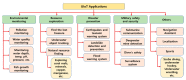
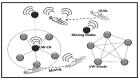
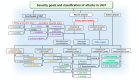
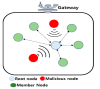
Owing to the hasty growth of communication technologies in the Underwater Internet of Things (UIoT), many researchers and industries focus on enhancing the existing technologies of UIoT systems for developing numerous applications such as oceanography, diver networks monitoring, deep-sea exploration and early warning systems. In a constrained UIoT environment, communication media such as acoustic, infrared (IR), visible light, radiofrequency (RF) and magnet induction (MI) are generally used to transmit information via digitally linked underwater devices. However, each medium has its technical limitations: for example, the acoustic medium has challenges such as narrow-channel bandwidth, low data rate, high cost, etc., and optical medium has challenges such as high absorption, scattering, long-distance data transmission, etc. Moreover, the malicious node can steal the underwater data by employing blackhole attacks, routing attacks, Sybil attacks, etc. Furthermore, due to heavyweight, the existing privacy and security mechanism of the terrestrial internet of things (IoT) cannot be applied directly to UIoT environment. Hence, this paper aims to provide a systematic review of recent trends, applications, communication technologies, challenges, security threats and privacy issues of UIoT system. Additionally, this paper highlights the methods of preventing the technical challenges and security attacks of the UIoT environment. Finally, this systematic review contributes much to the profit of researchers to analyze and improve the performance of services in UIoT applications.
Keywords: Underwater Internet of Things (UIoT); challenges; security and privacy; trends.
Conflict of interest statement
The authors declare no conflict of interest.
Figures





References
-
- NOAA, America’s Coastal & Ocean Agency How Much Water Is in the Ocean? [(accessed on 28 October 2021)]; Available online: https://oceanservice.noaa.gov/facts/oceanwater.html.
-
- Awan K.M., Shah P.A., Iqbal K., Gillani S., Ahmad W., Nam Y. Underwater Wireless Sensor Networks: A Review of Recent Issues and Challenges. Wirel. Commun. Mob. Comput. 2019;2019:6470359. doi: 10.1155/2019/6470359. - DOI
-
- Yang G., Dai L., Si G., Wang S., Wang S. Challenges and Security Issues in Underwater Wireless Sensor Networks. Procedia Comput. Sci. 2019;147:210–216. doi: 10.1016/j.procs.2019.01.225. - DOI
-
- Gussen C.M.G., Diniz P.S.R., Campos M.L.R., Martins W.A., Costa F.M., Gois J.N. A Survey of Underwater Wireless Communication Technologies. J. Commun. Inf. Syst. 2016;31:242–255. doi: 10.14209/jcis.2016.22. - DOI
-
- Zoksimovski A., Sexton D., Stojanovic M., Rappaport C. Underwater electromagnetic communications using conduction—Channel characterization. Ad Hoc Netw. 2015;34:42–51. doi: 10.1016/j.adhoc.2015.01.017. - DOI
Publication types
MeSH terms
LinkOut - more resources
Full Text Sources

