Microservice security: a systematic literature review
- PMID: 35111904
- PMCID: PMC8771803
- DOI: 10.7717/peerj-cs.779
Microservice security: a systematic literature review
Abstract
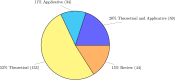
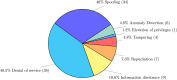
Microservices is an emerging paradigm for developing distributed systems. With their widespread adoption, more and more work investigated the relation between microservices and security. Alas, the literature on this subject does not form a well-defined corpus: it is spread over many venues and composed of contributions mainly addressing specific scenarios or needs. In this work, we conduct a systematic review of the field, gathering 290 relevant publications-at the time of writing, the largest curated dataset on the topic. We analyse our dataset along two lines: (a) quantitatively, through publication metadata, which allows us to chart publication outlets, communities, approaches, and tackled issues; (b) qualitatively, through 20 research questions used to provide an aggregated overview of the literature and to spot gaps left open. We summarise our analyses in the conclusion in the form of a call for action to address the main open challenges.
Keywords: Authentication; Authentication and authorization; Infrastructure-as-a-service; Intrusion detection and prevention; Privacy; Service composition; Service deployment; Service discovery; Software development; Threat model.
© 2022 Berardi et al.
Conflict of interest statement
The authors declare that they have no competing interests.
Figures


References
-
- Abidi S, Essafi M, Guegan CG, Fakhri M, Witti H, Ghezala HHB. A web service security governance approach based on dedicated micro-services. Procedia Computer Science. 2019;159(3):372–386. doi: 10.1016/j.procs.2019.09.192. - DOI
-
- Adam A, Alam MM. The fog cloud of things: a survey on concepts, architecture, standards, tools, and applications. Iternet of Thing. 2020;9:100177. doi: 10.1016/j.iot.2020.100177. - DOI
-
- Adedugbe O, Benkhelifa E, Campion R, Al-Obeidat F, Hani AB, Uchitha J. Leveraging cloud computing for the semantic web: review and trends. Soft Computing. 2019;24:5999–6014. doi: 10.1007/s00500-019-04559-2. - DOI
-
- Agarwal S, Malandrino F, Chiasserini CF, De S. VNF placement and resource allocation for the support of vertical services in 5g networks. IEEE/ACM Transactions on Networking. 2019;27(1):433–446. doi: 10.1109/TNET.2018.2890631. - DOI
-
- Ahmadvand M, Ibrahim A. Requirements reconciliation for scalable and secure microservice (de) composition. 2016 IEEE 24th International Requirements Engineering Conference Workshops (REW); Piscataway: IEEE; 2016. pp. 68–73.
LinkOut - more resources
Full Text Sources
Miscellaneous
