LSB-based pre-embedding video steganography with rotating & shifting poly-pattern block matrix
- PMID: 35111926
- PMCID: PMC8771781
- DOI: 10.7717/peerj-cs.843
LSB-based pre-embedding video steganography with rotating & shifting poly-pattern block matrix
Abstract
Background: In terms of data-hiding areas, video steganography is more advantageous compared to other steganography techniques since it uses video as its cover medium. For any video steganography, the good trade-off among robustness, imperceptibility, and payload must be created and maintained. Even though it has the advantage of capacity, video steganography has the robustness problem especially regarding spatial domain is used to implement it. Transformation operations and statistical attacks can harm secret data. Thus, the ideal video steganography technique must provide high imperceptibility, high payload, and resistance towards visual, statistical and transformation-based steganalysis attacks.
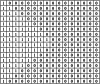
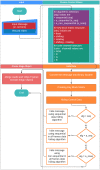
Methods: One of the most common spatial methods for hiding data within the cover medium is the Least Significant Bit (LSB) method. In this study, an LSB-based video steganography application that uses a poly-pattern key block matrix (KBM) as the key was proposed. The key is a 64 × 64 pixel block matrix that consists of 16 sub-pattern blocks with a pixel size of 16 × 16. To increase the security of the proposed approach, sub-patterns in the KBM are allowed to shift in four directions and rotate up to 270° depending on the user preference and logical operations. For additional security XOR and AND logical operations were used to determine whether to choose the next predetermined 64 × 64 pixel block or jump to another pixel block in the cover video frame to place a KBM to embed the secret data. The fact that the combination of variable KBM structure and logical operator for the secret data embedding distinguishes the proposed algorithm from previous video steganography studies conducted with LSB-based approaches.
Results: Mean Squared Error (MSE), Structural Similarity Index (SSIM) and Peak Signal-to-Noise Ratio (PSNR) parameters were calculated for the detection of the imperceptibility (or the resistance against visual attacks ) of the proposed algorithm. The proposed algorithm obtained the best MSE, SSIM and PSNR parameter values based on the secret message length as 0.00066, 0.99999, 80.01458 dB for 42.8 Kb of secret message and 0.00173, 0.99999, 75.72723 dB for 109 Kb of secret message, respectively. These results are better than the results of classic LSB and the studies conducted with LSB-based video steganography approaches in the literature. Since the proposed system allows an equal amount of data embedding in each video frame the data loss will be less in transformation operations. The lost data can be easily obtained from the entire text with natural language processing. The variable structure of the KBM, logical operators and extra security preventions makes the proposed system be more secure and complex. This increases the unpredictability and resistance against statistical attacks. Thus, the proposed method provides high imperceptibility and resistance towards visual, statistical and transformation-based attacks while acceptable even high payload.
Keywords: Cryptography; Data security; Information security; Key block matrix; Random number generation; Steganography; Video steganography.
©2022 Hacimurtazaoglu and Tutuncu.
Conflict of interest statement
The authors declare there are no competing interests.
Figures






References
-
- Akramullah S. Digital video concepts, methods, and metrics. Berkeley, CA: Apress; 2014. - DOI
-
- Alavianmehr MA, Rezaei M, Helfroush MS, Tashk A. A lossless data hiding scheme on video raw data robust against H.264/AVC compression. 2012 2nd international econference on computer and knowledge engineering (ICCKE); 2012. pp. 194–198. - DOI
-
- Chae J, Manjunath B. Data hiding in video. IEEE proceedings international conference on image processing (Cat. 99CH36348); Piscataway. 1999. - DOI
-
- Chitra S, Thoti N. Implementation of video steganography using hash function in LSB technique. International Journal of Engineering Research & Technology. 2013;2(11):3396–3403.
-
- Choudry KN, Wanjari A. A survey paper on video steganography. International Journal of Computer Science and Information Technologies (IJCSIT) 2015;6(3):2335–2338.
Associated data
LinkOut - more resources
Full Text Sources
Miscellaneous
