Integration of Healthcare 4.0 and blockchain into secure cloud-based electronic health records systems
- PMID: 35136707
- PMCID: PMC8813573
- DOI: 10.1007/s13204-021-02164-0
Integration of Healthcare 4.0 and blockchain into secure cloud-based electronic health records systems
Abstract
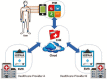
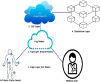
Since the last decade, cloud-based electronic health records (EHRs) have gained significant attention to enable remote patient monitoring. The recent development of Healthcare 4.0 using the Internet of Things (IoT) components and cloud computing to access medical operations remotely has gained the researcher's attention from a smart city perspective. Healthcare 4.0 mainly consisted of periodic medical data sensing, aggregation, data transmission, data sharing, and data storage. The sensitive and personal data of patients lead to several challenges while protecting it from hackers. Therefore storing, accessing, and sharing the patient medical information on the cloud needs security attention that data should not be compromised by the authorized user's components of E-healthcare systems. To achieve secure medical data storage, sharing, and accessing in cloud service provider, several cryptography algorithms are designed so far. However, such conventional solutions failed to achieve the trade-off between the requirements of EHR security solutions such as computational efficiency, service side verification, user side verifications, without the trusted third party, and strong security. Blockchain-based security solutions gained significant attention in the recent past due to the ability to provide strong security for data storage and sharing with the minimum computation efforts. The blockchain made focused on bitcoin technology among the researchers. Utilizing the blockchain which secure healthcare records management has been of recent interest. This paper presents the systematic study of modern blockchain-based solutions for securing medical data with or without cloud computing. We implement and evaluate the different methods using blockchain in this paper. According to the research studies, the research gaps, challenges, and future roadmap are the outcomes of this paper that boost emerging Healthcare 4.0 technology.
Keywords: Bitcoin; Blockchain; Cloud service provider; Data sharing; Data storage; Electronic heath records; Healthcare 4.0; Medical data; Security.
© King Abdulaziz City for Science and Technology 2022.
Conflict of interest statement
Conflict of interestAll authors declares that they have no conflict of interest.
Figures






References
-
- Abu-Rumman A (2021) Transformational leadership and human capital within the disruptive business environment of academia. World J Educ Technol 13(2):178–187. 10.18844/wjet.v13i2.5652
-
- Abu-Rumman A, Al Shraah A, Al-Madi F, et al. Entrepreneurial networks, entrepreneurial orientation, and performance of small and medium enterprises: are dynamic capabilities the missing link? J Innov Entrep. 2021;10:29. doi: 10.1186/s13731-021-00170-8. - DOI
-
- Aceto G, Botta A, de Donato W, Pescapè A. Cloud monitoring: a survey. Comput Netw. 2013;57(9):2093–2115. doi: 10.1016/j.comnet.2013.04.001. - DOI
-
- Alam Q, Malik SUR, Akhunzada A, Choo K-KR, Tabbasum S, Alam M. A cross tenant access control (CTAC) model for cloud computing: formal specification and verification. IEEE Trans Inf Forensics Secur. 2017;12(6):1259–1268. doi: 10.1109/tifs.2016.2646639. - DOI
-
- Aldiabat K, Kwekha Rashid AS, Talafha H, Karajeh A. The extent of smartphones users to adopt the use of cloud storage. J Comput Sci. 2018;14(12):1588–1598. doi: 10.3844/jcssp.2018.1588.1598. - DOI
LinkOut - more resources
Full Text Sources
Miscellaneous
