Internet of Things with Deep Learning-Based Face Recognition Approach for Authentication in Control Medical Systems
- PMID: 35190751
- PMCID: PMC8858039
- DOI: 10.1155/2022/5137513
Internet of Things with Deep Learning-Based Face Recognition Approach for Authentication in Control Medical Systems
Retraction in
-
Retracted: Internet of Things with Deep Learning-Based Face Recognition Approach for Authentication in Control Medical Systems.Comput Math Methods Med. 2023 Oct 11;2023:9757086. doi: 10.1155/2023/9757086. eCollection 2023. Comput Math Methods Med. 2023. PMID: 37867555 Free PMC article.
Abstract
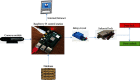
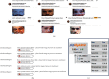
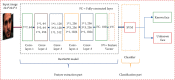
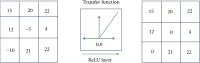
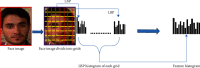
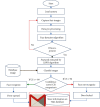
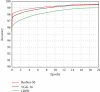
Internet of Things (IoT) with deep learning (DL) is drastically growing and plays a significant role in many applications, including medical and healthcare systems. It can help users in this field get an advantage in terms of enhanced touchless authentication, especially in spreading infectious diseases like coronavirus disease 2019 (COVID-19). Even though there is a number of available security systems, they suffer from one or more of issues, such as identity fraud, loss of keys and passwords, or spreading diseases through touch authentication tools. To overcome these issues, IoT-based intelligent control medical authentication systems using DL models are proposed to enhance the security factor of medical and healthcare places effectively. This work applies IoT with DL models to recognize human faces for authentication in smart control medical systems. We use Raspberry Pi (RPi) because it has low cost and acts as the main controller in this system. The installation of a smart control system using general-purpose input/output (GPIO) pins of RPi also enhanced the antitheft for smart locks, and the RPi is connected to smart doors. For user authentication, a camera module is used to capture the face image and compare them with database images for getting access. The proposed approach performs face detection using the Haar cascade techniques, while for face recognition, the system comprises the following steps. The first step is the facial feature extraction step, which is done using the pretrained CNN models (ResNet-50 and VGG-16) along with linear binary pattern histogram (LBPH) algorithm. The second step is the classification step which can be done using a support vector machine (SVM) classifier. Only classified face as genuine leads to unlock the door; otherwise, the door is locked, and the system sends a notification email to the home/medical place with detected face images and stores the detected person name and time information on the SQL database. The comparative study of this work shows that the approach achieved 99.56% accuracy compared with some different related methods.
Copyright © 2022 Tahir Hussain et al.
Conflict of interest statement
There are no conflicts of interest associated with publishing this paper.
Figures















References
-
- Nareshkumar R., Kamat A., Shinde D. Smart door security control system using Raspberry Pi. International Journal of Innovations & Advancement in Computer Science (IJIACS) . 2017;6:499–503.
-
- Najmurrokhman A., Kusnandar K., Krama A. B., Djamal E. C., Rahim R. Development of a secured room access system based on face recognition using Raspberry Pi and Android based smartphone. EDP Sciences . 2018;197:p. 11008. doi: 10.1051/matecconf/201819711008. - DOI
-
- Perdana A. B., Prahara A. Face recognition using light-convolutional neural networks based on modified Vgg16 model. 2019 International Conference of Computer Science and Information Technology (ICoSNIKOM); 2019; Medan, Indonesia. pp. 1–4. - DOI
-
- Dabhi M. K., Pancholi B. K. Face detection system based on Viola-Jones algorithm. International Journal of Science and Research (IJSR) . 2016;5(4):62–64. doi: 10.21275/v5i4.NOV162465. - DOI
-
- Agarwal M., Agrawal H., Jain N., Kumar M. Face recognition using principle component analysis, eigenface and neural network. 2010 International Conference on Signal Acquisition and Processing; 2010; Bangalore, India. pp. 310–314. - DOI
Publication types
MeSH terms
LinkOut - more resources
Full Text Sources
Research Materials
Miscellaneous

