Revisiting the Feasibility of Public Key Cryptography in Light of IIoT Communications
- PMID: 35408176
- PMCID: PMC9003447
- DOI: 10.3390/s22072561
Revisiting the Feasibility of Public Key Cryptography in Light of IIoT Communications
Abstract
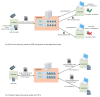
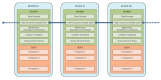
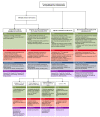
Digital certificates are regarded as the most secure and scalable way of implementing authentication services in the Internet today. They are used by most popular security protocols, including Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS). The lifecycle management of digital certificates relies on centralized Certification Authority (CA)-based Public Key Infrastructures (PKIs). However, the implementation of PKIs and certificate lifecycle management procedures in Industrial Internet of Things (IIoT) environments presents some challenges, mainly due to the high resource consumption that they imply and the lack of trust in the centralized CAs. This paper identifies and describes the main challenges to implement certificate-based public key cryptography in IIoT environments and it surveys the alternative approaches proposed so far in the literature to address these challenges. Most proposals rely on the introduction of a Trusted Third Party to aid the IIoT devices in tasks that exceed their capacity. The proposed alternatives are complementary and their application depends on the specific challenge to solve, the application scenario, and the capacities of the involved IIoT devices. This paper revisits all these alternatives in light of industrial communication models, identifying their strengths and weaknesses, and providing an in-depth comparative analysis.
Keywords: ABE; DTLS; IIoT; PKI; X.509; blockchain.
Conflict of interest statement
The authors declare no conflict of interest.
Figures




References
-
- Nur N.M., Yusnani M.Y., Mohammed A.S., Hashim H. Hybrid cryptographic approach for internet of things applications: A review. J. Inf. Commun. Technol. 2020;19:279–319.
-
- Fernández-Caramés T.M. From Pre-Quantum to Post-Quantum IoT Security: A Survey on Quantum-Resistant Cryptosystems for the Internet of Things. IEEE Internet Things J. 2020;7:6457–6480. doi: 10.1109/JIOT.2019.2958788. - DOI
-
- Wang P., Li B., Shi H., Shen Y., Wang D. Revisiting Anonymous Two-Factor Authentication Schemes for IoT-Enabled Devices in Cloud Computing Environments. Secur. Commun. Netw. 2019;2019:2516963. doi: 10.1155/2019/2516963. - DOI
Publication types
MeSH terms
LinkOut - more resources
Full Text Sources

