Towards a Security Reference Architecture for NFV
- PMID: 35632161
- PMCID: PMC9146665
- DOI: 10.3390/s22103750
Towards a Security Reference Architecture for NFV
Abstract
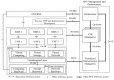
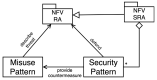
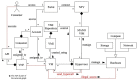
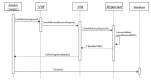
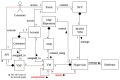
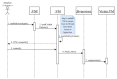
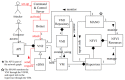
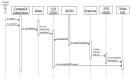
Network function virtualization (NFV) is an emerging technology that is becoming increasingly important due to its many advantages. NFV transforms legacy hardware-based network infrastructure into software-based virtualized networks. This transformation increases the flexibility and scalability of networks, at the same time reducing the time for the creation of new networks. However, the attack surface of the network increases, which requires the definition of a clear map of where attacks may happen. ETSI standards precisely define many security aspects of this architecture, but these publications are very long and provide many details which are not of interest to software architects. We start by conducting threat analysis of some of the NFV use cases. The use cases serve as scenarios where the threats to the architecture can be enumerated. Representing threats as misuse cases that describe the modus operandi of attackers, we can find countermeasures to them in the form of security patterns, and we can build a security reference architecture (SRA). Until now, only imprecise models of NFV architectures existed; by making them more detailed and precise it is possible to handle not only security but also safety and reliability, although we do not explore those aspects. Because security is a global property that requires a holistic approach, we strongly believe that architectural models are fundamental to produce secure networks and allow us to build networks which are secure by design. The resulting SRA defines a roadmap to implement secure concrete architectures.
Keywords: ETSI; cloud computing; network function virtualization; patterns; reference architecture; security reference architecture; virtual machine environment; virtual network function.
Conflict of interest statement
The authors declare no conflict of interest.
Figures

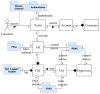
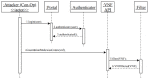
References
-
- Chiosi M., Clarke D., Willis P., Reid A., Feger J., Bugenhagen M., Khan W., Cui C., Deng H., Chen C. Network Functions Virtualisation (NFV): Network Operator Perspectives on Industry Progress; Proceedings of the SDN & OpenFlow World Congress; Düsseldorf, Germany. 14–17 October 2013.
-
- ETSI . Network Functions Virtualisation (NFV); Infrastructure Overview. ETSI; Sophia Antipolis, France: 2015.
-
- ETSI . Network Functions Virtualisation (NFV); Architectural Framework. ETSI; Sophia Antipolis, France: 2014.
-
- Milenkoski A., Jaeger B., Raina K., Harris M., Chaudhry S., Chasiri S., David V., Liu W. Security Position Paper: Network Function Virtualization. Cloud Security Alliance-Virtualization Working Group; 2016. [(accessed on 30 April 2022)]. Available online: https://cloudsecurityalliance.org/artifacts/security-position-paper-netw...
-
- Ahmad I., Kumar T., Liyanage M., Okwuibe J., Ylianttila M., Gurtov A. Overview of 5G Security Challenges and Solutions. IEEE Commun. Stand. Mag. 2018;2:36–43. doi: 10.1109/MCOMSTD.2018.1700063. - DOI
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources

