A double scrambling-DNA row and column closed loop image encryption algorithm based on chaotic system
- PMID: 35819964
- PMCID: PMC9275730
- DOI: 10.1371/journal.pone.0267094
A double scrambling-DNA row and column closed loop image encryption algorithm based on chaotic system
Abstract
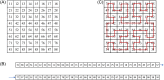
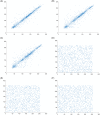
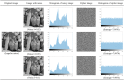
In this paper, a dynamic update algorithm of double scrambling-DNA row and column closed loop based on chaotic system is proposed. The classical scrambling and diffusion structure are used in the whole process. In the scrambling stage, a new pixel reconstruction method is proposed by combining the Hilbert curve with Knuth-Durstenfeld shuffle algorithm to overcome the shortcoming of nearby storage of Hilbert curve. This method reconstructs the pixel matrix of one-dimensional vector according to the Hilbert curve coding method, and achieves good scrambling effect, while reducing its time complexity and space complexity. In the diffusion stage, combining the plaintext row, the ciphertext row and the key row, and taking advantage of the parallel computing power and high storage density of the DNA encoding, the existing block diffusion operation is improved, and the two-round diffusion of the DNA encoding is proposed. When the last line of ciphertext is generated, the first line of ciphertext is updated and the closed-loop dynamic update of the encryption system is realized. Finally, SHA-256 is used to give the secret key and calculate the initial value of the chaotic system. The simulation results show that the "double scrambling-DNA row and column closed loop dynamic" update algorithm proposed in this paper can effectively improve the efficiency of information transmission and have high security.
Conflict of interest statement
The authors have declared that no competing interests exist.
Figures










Similar articles
-
An Image Encryption Algorithm Based on Improved Hilbert Curve Scrambling and Dynamic DNA Coding.Entropy (Basel). 2023 Aug 8;25(8):1178. doi: 10.3390/e25081178. Entropy (Basel). 2023. PMID: 37628208 Free PMC article.
-
Secure Image Encryption Algorithm Based on Hyperchaos and Dynamic DNA Coding.Entropy (Basel). 2020 Jul 15;22(7):772. doi: 10.3390/e22070772. Entropy (Basel). 2020. PMID: 33286544 Free PMC article.
-
A Novel Chaotic Image Encryption Algorithm Based on Latin Square and Random Shift.Comput Intell Neurosci. 2021 Sep 6;2021:2091053. doi: 10.1155/2021/2091053. eCollection 2021. Comput Intell Neurosci. 2021. PMID: 34531907 Free PMC article.
-
Multi-Image Encryption Algorithm Based on Cascaded Modulation Chaotic System and Block-Scrambling-Diffusion.Entropy (Basel). 2022 Jul 31;24(8):1053. doi: 10.3390/e24081053. Entropy (Basel). 2022. PMID: 36010719 Free PMC article.
-
Cryptanalyzing and Improving an Image Encryption Algorithm Based on Chaotic Dual Scrambling of Pixel Position and Bit.Entropy (Basel). 2023 Feb 22;25(3):400. doi: 10.3390/e25030400. Entropy (Basel). 2023. PMID: 36981290 Free PMC article.
Cited by
-
A double encryption protection algorithm for stem cell bank privacy data based on improved AES and chaotic encryption technology.PLoS One. 2023 Oct 25;18(10):e0293418. doi: 10.1371/journal.pone.0293418. eCollection 2023. PLoS One. 2023. PMID: 37878640 Free PMC article.
-
Enhancing AES image encryption with a three-dimensional hyperchaotic system for increased security and efficiency.PLoS One. 2025 Jul 18;20(7):e0328297. doi: 10.1371/journal.pone.0328297. eCollection 2025. PLoS One. 2025. PMID: 40680055 Free PMC article.
References
-
- Gong LH, Qiu KD, Deng CZ, Zhou NR. An image compression and encryption algorithm based on chaotic system and compressive sensing. Optics and Laser Technology. 2019. Jul;115(6):257–267. doi: 10.1016/j.optlastec.2019.01.039 - DOI
-
- Song YJ,Zhu ZL,Zhang W, et al.. Joint image compression–encryption scheme using entropy coding and compressive sensing. Nonlinear Dynamics. 2019. Feb;95(3):2235–2261. doi: 10.1007/s11071-018-4689-9 - DOI
-
- Yu SS,Zhou NR, Gong LH, Nie Z. Optical image encryption algorithm based on phase-truncated short-time fractional Fourier transform and hyper-chaotic system. Optics and Lasers in Engineering. 2020. Jan;124(6):105816–105827. doi: 10.1016/j.optlaseng.2019.105816 - DOI
-
- Farah MB,Guesmi R,Kachouri A, Samet M. A novel chaos based optical image encryption using fractional Fourier transform and DNA sequence operation. Optics and Laser Technology. 2020. Jan;121(7):577–589. 10.1016/j.optlastec.2019.105777 - DOI
-
- Xian YJ, Wang XY. Fractal sorting matrix and its application on chaotic image encryption. Information Sciences. 2021. Feb;547(3):1154–1169. doi: 10.1016/j.ins.2020.09.055 - DOI
MeSH terms
Substances
LinkOut - more resources
Full Text Sources

