A device-independent quantum key distribution system for distant users
- PMID: 35896650
- PMCID: PMC9329124
- DOI: 10.1038/s41586-022-04891-y
A device-independent quantum key distribution system for distant users
Abstract
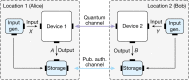
Device-independent quantum key distribution (DIQKD) enables the generation of secret keys over an untrusted channel using uncharacterized and potentially untrusted devices1-9. The proper and secure functioning of the devices can be certified by a statistical test using a Bell inequality10-12. This test originates from the foundations of quantum physics and also ensures robustness against implementation loopholes13, thereby leaving only the integrity of the users' locations to be guaranteed by other means. The realization of DIQKD, however, is extremely challenging-mainly because it is difficult to establish high-quality entangled states between two remote locations with high detection efficiency. Here we present an experimental system that enables for DIQKD between two distant users. The experiment is based on the generation and analysis of event-ready entanglement between two independently trapped single rubidium atoms located in buildings 400 metre apart14. By achieving an entanglement fidelity of [Formula: see text] and implementing a DIQKD protocol with random key basis15, we observe a significant violation of a Bell inequality of S = 2.578(75)-above the classical limit of 2-and a quantum bit error rate of only 0.078(9). For the protocol, this results in a secret key rate of 0.07 bits per entanglement generation event in the asymptotic limit, and thus demonstrates the system's capability to generate secret keys. Our results of secure key exchange with potentially untrusted devices pave the way to the ultimate form of quantum secure communications in future quantum networks.
© 2022. The Author(s).
Conflict of interest statement
The authors declare no competing interests.
Figures




Comment in
-
Quantum entanglement provides a key to improved security.Nature. 2022 Jul;607(7920):662-664. doi: 10.1038/d41586-022-01987-3. Nature. 2022. PMID: 35896640 No abstract available.
References
-
- Mayers, D. and Yao, A. Quantum cryptography with imperfect apparatus. In Proc. 39th Annual Symposium on Foundations of Computer Science 503–509 (IEEE, 1998).
-
- Pironio S. Device-independent quantum key distribution secure against collective attacks. New J. Phys. 2009;11:045021. doi: 10.1088/1367-2630/11/4/045021. - DOI
Publication types
LinkOut - more resources
Full Text Sources

