Towards an Effective Intrusion Detection Model Using Focal Loss Variational Autoencoder for Internet of Things (IoT)
- PMID: 35957379
- PMCID: PMC9371235
- DOI: 10.3390/s22155822
Towards an Effective Intrusion Detection Model Using Focal Loss Variational Autoencoder for Internet of Things (IoT)
Abstract
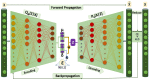
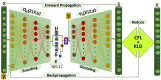
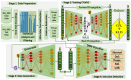
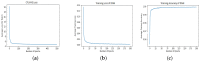
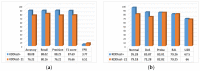
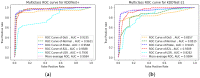
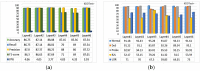
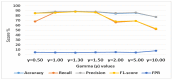
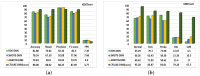
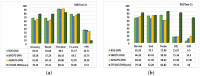
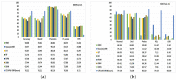
As the range of security attacks increases across diverse network applications, intrusion detection systems are of central interest. Such detection systems are more crucial for the Internet of Things (IoT) due to the voluminous and sensitive data it produces. However, the real-world network produces imbalanced traffic including different and unknown attack types. Due to this imbalanced nature of network traffic, the traditional learning-based detection techniques suffer from lower overall detection performance, higher false-positive rate, and lower minority-class attack detection rates. To address the issue, we propose a novel deep generative-based model called Class-wise Focal Loss Variational AutoEncoder (CFLVAE) which overcomes the data imbalance problem by generating new samples for minority attack classes. Furthermore, we design an effective and cost-sensitive objective function called Class-wise Focal Loss (CFL) to train the traditional Variational AutoEncoder (VAE). The CFL objective function focuses on different minority class samples and scrutinizes high-level feature representation of observed data. This leads the VAE to generate more realistic, diverse, and quality intrusion data to create a well-balanced intrusion dataset. The balanced dataset results in improving the intrusion detection accuracy of learning-based classifiers. Therefore, a Deep Neural Network (DNN) classifier with a unique architecture is then trained using the balanced intrusion dataset to enhance the detection performance. Moreover, we utilize a challenging and highly imbalanced intrusion dataset called NSL-KDD to conduct an extensive experiment with the proposed model. The results demonstrate that the proposed CFLVAE with DNN (CFLVAE-DNN) model obtains promising performance in generating realistic new intrusion data samples and achieves superior intrusion detection performance. Additionally, the proposed CFLVAE-DNN model outperforms several state-of-the-art data generation and traditional intrusion detection methods. Specifically, the CFLVAE-DNN achieves 88.08% overall intrusion detection accuracy and 3.77% false positive rate. More significantly, it obtains the highest low-frequency attack detection rates for U2R (79.25%) and R2L (67.5%) against all the state-of-the-art algorithms.
Keywords: Class-wise Focal Loss; Deep Neural Network; Internet of Things; Variational AutoEncoder; data imbalance; intrusion detection.
Conflict of interest statement
The authors declare no conflict of interest. The founding sponsors had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, and in the decision to publish the results.
Figures


Similar articles
-
Improving the Classification Effectiveness of Intrusion Detection by Using Improved Conditional Variational AutoEncoder and Deep Neural Network.Sensors (Basel). 2019 Jun 2;19(11):2528. doi: 10.3390/s19112528. Sensors (Basel). 2019. PMID: 31159512 Free PMC article.
-
Optimal intrusion detection for imbalanced data using Bagging method with deep neural network optimized by flower pollination algorithm.PeerJ Comput Sci. 2025 Mar 17;11:e2745. doi: 10.7717/peerj-cs.2745. eCollection 2025. PeerJ Comput Sci. 2025. PMID: 40134887 Free PMC article.
-
VAE-WACGAN: An Improved Data Augmentation Method Based on VAEGAN for Intrusion Detection.Sensors (Basel). 2024 Sep 18;24(18):6035. doi: 10.3390/s24186035. Sensors (Basel). 2024. PMID: 39338780 Free PMC article.
-
A Deep Learning-Based Intrusion Detection System for MQTT Enabled IoT.Sensors (Basel). 2021 Oct 22;21(21):7016. doi: 10.3390/s21217016. Sensors (Basel). 2021. PMID: 34770322 Free PMC article. Review.
-
IoT Intrusion Detection Taxonomy, Reference Architecture, and Analyses.Sensors (Basel). 2021 Sep 26;21(19):6432. doi: 10.3390/s21196432. Sensors (Basel). 2021. PMID: 34640752 Free PMC article. Review.
Cited by
-
An Adaptive Temporal Convolutional Network Autoencoder for Malicious Data Detection in Mobile Crowd Sensing.Sensors (Basel). 2024 Apr 7;24(7):2353. doi: 10.3390/s24072353. Sensors (Basel). 2024. PMID: 38610563 Free PMC article.
-
HiViT-IDS: An Efficient Network Intrusion Detection Method Based on Vision Transformer.Sensors (Basel). 2025 Mar 12;25(6):1752. doi: 10.3390/s25061752. Sensors (Basel). 2025. PMID: 40292892 Free PMC article.
References
-
- Alaba F.A., Othman M., Hashem I.A.T., Alotaibi F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017;88:10–28. doi: 10.1016/j.jnca.2017.04.002. - DOI
-
- Khanam S., Ahmedy I.B., Idris M.Y.I., Jaward M.H., Sabri A.Q.B.M. A survey of security challenges, attacks taxonomy and advanced countermeasures in the internet of things. IEEE Access. 2020;8:219709–219743. doi: 10.1109/ACCESS.2020.3037359. - DOI
-
- Kovacs E. Flaws in Smart City Systems Can Allow Hackers to Cause Panic. [(accessed on 22 September 2021)]. Available online: https://www.securityweek.com/flaws-smart-city-systems-can-allow-hackers-....
-
- Vinayakumar R., Soman K., Poornachandran P. Evaluating effectiveness of shallow and deep networks to intrusion detection system; Proceedings of the 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI); Udupi, India. 13–16 September 2017; pp. 1282–1289.
-
- Vinayakumar R., Alazab M., Soman K., Poornachandran P., Al-Nemrat A., Venkatraman S. Deep learning approach for intelligent intrusion detection system. IEEE Access. 2019;7:41525–41550. doi: 10.1109/ACCESS.2019.2895334. - DOI
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources
Research Materials

