A strong construction of S-box using Mandelbrot set an image encryption scheme
- PMID: 36262157
- PMCID: PMC9575852
- DOI: 10.7717/peerj-cs.892
A strong construction of S-box using Mandelbrot set an image encryption scheme
Abstract
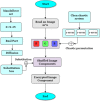
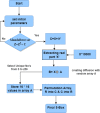
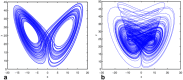
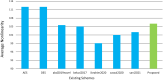
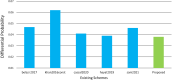
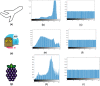
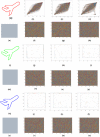
The substitution box (S-box) plays a vital role in creating confusion during the encryption process of digital data. The quality of encryption schemes depends upon the S-box. There have been several attempts to enhance the quality of the S-box by using fractal chaotic mechanisms. However, there is still weakness in the robustness against cryptanalysis of fractal-based S-boxes. Due to their chaotic behavior, fractals are frequently employed to achieve randomness by confusion and diffusion process. A complex number-based S-box and a chaotic map diffusion are proposed to achieve high nonlinearity and low correlation. This study proposed a Mandelbrot set S-box construction based on the complex number and Chen chaotic map for resisting cryptanalytic attacks by creating diffusion in our proposed algorithm. The cryptosystem was built on the idea of substitution permutation networks (SPN). The complex nature of the proposed S-box makes it more random than other chaotic maps. The robustness of the proposed system was analyzed by different analysis properties of the S-box, such as nonlinearity, strict avalanche criterion, Bit independent criterion, and differential and linear probability. Moreover, to check the strength of the proposed S-box against differential and brute force attacks, we performed image encryption with the proposed S-box. The security analysis was performed, including statistical attack analysis and NIST analysis. The analysis results show that the proposed system achieves high-security standards than existing schemes.
Keywords: Chen chaotic system; Cryptosystem; Image encryption; Mandelbrot set; Substitution-box.
©2022 Aslam et al.
Conflict of interest statement
The authors declare there are no competing interests.
Figures




References
-
- Abd EL-Latif AA, Abd-El-Atty B, Venegas-Andraca SE. A novel image steganography technique based on quantum substitution boxes. Optics & Laser Technology. 2019;116:92–102. doi: 10.1016/j.optlastec.2019.03.005. - DOI
-
- Aboytes-González J, Murguía J, Mejía-Carlos M, González-Aguilar H, Ramírez-Torres M. Design of a strong S-box based on a matrix approach. Nonlinear Dynamics. 2018;94(3):2003–2012. doi: 10.1007/s11071-018-4471-z. - DOI
-
- Azam NA, Ullah I, Hayat U. A fast and secure public-key image encryption scheme based on Mordell elliptic curves. Optics and Lasers in Engineering. 2021;137:106371. doi: 10.1016/j.optlaseng.2020.106371. - DOI
LinkOut - more resources
Full Text Sources
