The Face Deepfake Detection Challenge
- PMID: 36286357
- PMCID: PMC9605671
- DOI: 10.3390/jimaging8100263
The Face Deepfake Detection Challenge
Abstract
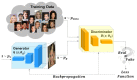
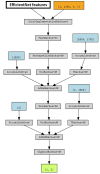
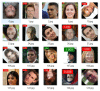
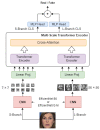
Multimedia data manipulation and forgery has never been easier than today, thanks to the power of Artificial Intelligence (AI). AI-generated fake content, commonly called Deepfakes, have been raising new issues and concerns, but also new challenges for the research community. The Deepfake detection task has become widely addressed, but unfortunately, approaches in the literature suffer from generalization issues. In this paper, the Face Deepfake Detection and Reconstruction Challenge is described. Two different tasks were proposed to the participants: (i) creating a Deepfake detector capable of working in an "in the wild" scenario; (ii) creating a method capable of reconstructing original images from Deepfakes. Real images from CelebA and FFHQ and Deepfake images created by StarGAN, StarGAN-v2, StyleGAN, StyleGAN2, AttGAN and GDWCT were collected for the competition. The winning teams were chosen with respect to the highest classification accuracy value (Task I) and "minimum average distance to Manhattan" (Task II). Deep Learning algorithms, particularly those based on the EfficientNet architecture, achieved the best results in Task I. No winners were proclaimed for Task II. A detailed discussion of teams' proposed methods with corresponding ranking is presented in this paper.
Keywords: deep learning; deepfake challenge; deepfake detection; deepfake reconstruction; discrete cosine transform; transformer networks.
Conflict of interest statement
The authors declare no conflict of interest.
Figures






References
-
- Goodfellow I., Pouget-Abadie J., Mirza M., Xu B., Warde-Farley D., Ozair S., Courville A., Bengio Y. Generative Adversarial Nets; Proceedings of the Advances in Neural Information Processing Systems; Montreal, QC, Canada. 8–13 December 2014; pp. 2672–2680.
-
- Guarnera L., Giudice O., Battiato S. Deepfake Style Transfer Mixture: A First Forensic Ballistics Study on Synthetic Images; Proceedings of the International Conference on Image Analysis and Processing; Lecce, Italy. 23–27 May 2022; Berlin/Heidelberg, Germany: Springer; 2022. pp. 151–163.
-
- Giudice O., Paratore A., Moltisanti M., Battiato S. A Classification Engine for Image Ballistics of Social Data; Proceedings of the International Conference on Image Analysis and Processing; Catania, Italy. 11–15 September 2017; Berlin/Heidelberg, Germany: Springer; 2017. pp. 625–636.
-
- Wang X., Guo H., Hu S., Chang M.C., Lyu S. GAN-generated Faces Detection: A Survey and New Perspectives. arXiv. 20222202.07145
-
- Verdoliva L. Media Forensics and Deepfakes: An Overview. IEEE J. Sel. Top. Signal Process. 2020;14:910–932. doi: 10.1109/JSTSP.2020.3002101. - DOI
LinkOut - more resources
Full Text Sources

