Gaussian Multiuser Wiretap Channels in the Presence of a Jammer-Aided Eavesdropper
- PMID: 36359685
- PMCID: PMC9689472
- DOI: 10.3390/e24111595
Gaussian Multiuser Wiretap Channels in the Presence of a Jammer-Aided Eavesdropper
Abstract
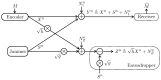
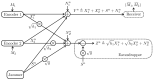
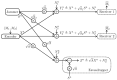
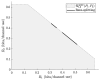
This paper considers secure communication in the presence of an eavesdropper and a malicious jammer. The jammer is assumed to be oblivious of the communication signals emitted by the legitimate transmitter(s) but can employ any jamming strategy subject to a given power constraint and shares her jamming signal with the eavesdropper. Four such models are considered: (i) the Gaussian point-to-point wiretap channel; (ii) the Gaussian multiple-access wiretap channel; (iii) the Gaussian broadcast wiretap channel; and (iv) the Gaussian symmetric interference wiretap channel. The use of pre-shared randomness between the legitimate users is not allowed in our models. Inner and outer bounds are derived for these four models. For (i), the secrecy capacity is obtained. For (ii) and (iv) under a degraded setup, the optimal secrecy sum-rate is characterized. Finally, for (iii), ranges of model parameter values for which the inner and outer bounds coincide are identified.
Keywords: Gaussian broadcast wiretap channel; Gaussian multiple-access wiretap channel; Gaussian wiretap channel; jamming; secure communication.
Conflict of interest statement
The authors declare no conflict of interest.
Figures
References
-
- Csiszár I., Narayan P. Capacity of the Gaussian arbitrarily varying channel. IEEE Trans. Inf. Theory. 1991;37:18–26. doi: 10.1109/18.61125. - DOI
-
- Leung-Yan-Cheong S., Hellman M. The Gaussian wire-tap channel. IEEE Trans. Inf. Theory. 1978;24:451–456. doi: 10.1109/TIT.1978.1055917. - DOI
-
- Tekin E., Yener A. The general Gaussian multiple-access and two-way wiretap channels: Achievable rates and cooperative jamming. IEEE Trans. Inf. Theory. 2008;54:2735–2751. doi: 10.1109/TIT.2008.921680. - DOI
-
- Bagherikaram G., Motahari A.S., Khandani A.K. Secure broadcasting: The secrecy rate region; Proceedings of the Communication, Control, and Computing, 2008 46th Annual Allerton Conference; Monticello, IL, USA. 23–26 September 2008; pp. 834–841.
-
- Grant A., Rimoldi B., Urbanke R., Whiting P. Rate-splitting multiple access for discrete memoryless channels. IEEE Trans. Inf. Theory. 2001;47:873–890. doi: 10.1109/18.915637. - DOI
LinkOut - more resources
Full Text Sources

