Detection of Middlebox-Based Attacks in Healthcare Internet of Things Using Multiple Machine Learning Models
- PMID: 36479020
- PMCID: PMC9722287
- DOI: 10.1155/2022/2037954
Detection of Middlebox-Based Attacks in Healthcare Internet of Things Using Multiple Machine Learning Models
Abstract
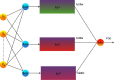
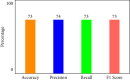
The huge number of network traffic data, the abundance of available network features, and the diversity of cyber-attack patterns mean that intrusion detection remains difficult even though many earlier efforts have succeeded in building the Internet of Healthcare Things (IoHT). The implementation of an effective algorithm to filter out most of the probable outliers of Round Trip Time (RTT) of packets recorded in the Internet environment is urgently required. Congestion and interference in networks can arise when numerous biosensors in an IoHT system all attempt to communicate at once. Internet of Health Things networks are susceptible to both intra- and internetwork interference. In this research, the Server-Side Includes (SSI) attack is a key issue because it allows for network compromise as part of Internal Attacks. Despite recent advancements, SSI detection remains difficult due to the vast amounts of network traffic data, the abundance of network features, and the diversity of cyber-attack patterns (DDoS, DoS, Satan, spoofing, etc.). With the help of sensors, physiological data may be collected and sent to distant servers, where they can be analyzed in real time by doctors to help them catch diseases in their earliest stages. This is made possible by the Internet of medical things (IoMT). Wireless data transfer, however, leaves it vulnerable to hackers, especially if the data being transferred are particularly private or sensitive. Security measures designed for devices with more storage space and processing power will not work on those with less. However, machine learning for intrusion detection can give a tailored security response to the needs of IoMT systems. For SSI detection, current methods are either inefficient because of the large number of packets that need to be caught and analyzed or unsuccessful because of outlier values in the RTTs obtained from the captured TCP packets. To the same end, "downstream detection" refers to the process of calculating the total length of all connections made after a certain point. As a means of improving the SSI detection algorithm's throughput in a network environment, packet RTT outliers will be eliminated. Flow records are used as inputs by flow-based NIDS to determine whether or not a given flow is malicious. In order to detect middlebox-based attacks from two Medical Health IoT datasets, this paper proposes a unique architecture of explainable neural networks (XNN). The model's accuracy in classifying attacks in dataset 1 of the IoHT is 99.7%t, besides achieving 99.4% accuracy in categorising attacks on IoHT dataset 2.
Copyright © 2022 Abdulwahid Al Abdulwahid.
Conflict of interest statement
The author declares that he has no conflicts of interest.
Figures

















References
-
- Rouzbahani H. M., Karimipour H., Lei L. Multi-layer defense algorithm against deep reinforcement learning-based intruders in smart grids. TechRxiv . 2022:1–10.
-
- A D., Keerthana K., Kiruthikanjali N., Nandhini G., Yuvaraj G. Secured smart healthcare monitoring system based on IOT. SSRN Electronic Journal . 2017;5(20):5–7. doi: 10.2139/ssrn.2941100. - DOI
-
- Meng W., Li W., Zhu L. Enhancing Medical Smartphone Networks via Blockchain-Based Trust Management against Insider Attacks. IEEE Transactions on Engineering Management . 2020;67(4):1377–1386. doi: 10.1109/TEM.2019.2921736. - DOI
-
- Butt S. A., Diaz-Martinez J. L., Jamal T., Ali A., De-La-Hoz-Franco E., Shoaib M. IoT smart health security threats. Proceedings of the 2019 19th International Conference on Computational Science and Its Applications (ICCSA); July 2019; Petersburg, Russia. - DOI
MeSH terms
LinkOut - more resources
Full Text Sources
Research Materials

