Getting Smarter about Smart Cities: Improving Data Security and Privacy through Compliance
- PMID: 36502039
- PMCID: PMC9738399
- DOI: 10.3390/s22239338
Getting Smarter about Smart Cities: Improving Data Security and Privacy through Compliance
Abstract
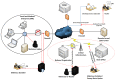
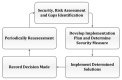
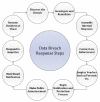
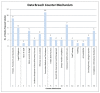
Smart cities assure the masses a higher quality of life through digital interconnectivity, leading to increased efficiency and accessibility in cities. In addition, a huge amount of data is being exchanged through smart devices, networks, cloud infrastructure, big data analysis and Internet of Things (IoT) applications in the various private and public sectors, such as critical infrastructures, financial sectors, healthcare, and Small and Medium Enterprises (SMEs). However, these sectors require maintaining certain security mechanisms to ensure the confidentiality and integrity of personal and critical information. However, unfortunately, organizations fail to maintain their security posture in terms of security mechanisms and controls, which leads to data breach incidents either intentionally or inadvertently due to the vulnerabilities in their information management systems that either malicious insiders or attackers exploit. In this paper, we highlight the importance of data breaches and issues related to information leakage incidents. In particular, the impact of data breaching incidents and the reasons contributing to such incidents affect the citizens' well-being. In addition, this paper also discusses various preventive measures such as security mechanisms, laws, standards, procedures, and best practices, including follow-up mitigation strategies.
Keywords: Personal Identity Information (PII); compliance; data breaches; information security policies and procedures; vulnerabilities.
Conflict of interest statement
The authors declare no conflict of interest.
Figures



Similar articles
-
A Framework for Malicious Traffic Detection in IoT Healthcare Environment.Sensors (Basel). 2021 Apr 26;21(9):3025. doi: 10.3390/s21093025. Sensors (Basel). 2021. PMID: 33925813 Free PMC article.
-
An Efficient Framework for Securing the Smart City Communication Networks.Sensors (Basel). 2022 Apr 15;22(8):3053. doi: 10.3390/s22083053. Sensors (Basel). 2022. PMID: 35459038 Free PMC article.
-
Strengthening Privacy and Data Security in Biomedical Microelectromechanical Systems by IoT Communication Security and Protection in Smart Healthcare.Sensors (Basel). 2023 Nov 3;23(21):8944. doi: 10.3390/s23218944. Sensors (Basel). 2023. PMID: 37960646 Free PMC article.
-
A Comparative Analysis on Blockchain versus Centralized Authentication Architectures for IoT-Enabled Smart Devices in Smart Cities: A Comprehensive Review, Recent Advances, and Future Research Directions.Sensors (Basel). 2022 Jul 10;22(14):5168. doi: 10.3390/s22145168. Sensors (Basel). 2022. PMID: 35890848 Free PMC article. Review.
-
Internet of Things: Security and Solutions Survey.Sensors (Basel). 2022 Sep 30;22(19):7433. doi: 10.3390/s22197433. Sensors (Basel). 2022. PMID: 36236531 Free PMC article. Review.
Cited by
-
Utilizing Artificial neural networks (ANN) to regulate Smart cities for sustainable Urban Development and Safeguarding Citizen rights.Sci Rep. 2024 Dec 30;14(1):31592. doi: 10.1038/s41598-024-76964-z. Sci Rep. 2024. PMID: 39738236 Free PMC article.
References
-
- Tang V., Cheng S.W., Choy K.L., Siu P.K., Ho G.T., Lam H.Y. An intelligent medical replenishment system for managing the medical resources in the healthcare industry; Proceedings of the 2016 IEEE International Conference on Fuzzy Systems (FUZZ-IEEE 2016); Vancouver, BC, Canada. 24–29 July 2016; - DOI
-
- Mehmood A., Natgunanathan I., Xiang Y., Hua G., Guo S. Protection of Big Data Privacy. IEEE Access. 2016;4:1821–1834. doi: 10.1109/ACCESS.2016.2558446. - DOI
-
- Siddiqui F., Matloob G. Data at rest and it’s security solutions—A survey. Int. J. Adv. Res. Comput. Sci. 2017;8:1491–1493.
-
- Kim G.H., Trimi S., Chung J.H. Big-data applications in the government sector. Commun. ACM. 2014;57:78–85. doi: 10.1145/2500873. - DOI
-
- Jang-Jaccard J., Nepal S. A survey of emerging threats in cybersecurity. J. Comput. Syst. Sci. 2014;80:973–993. doi: 10.1016/j.jcss.2014.02.005. - DOI
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources

