AES Based White Box Cryptography in Digital Signature Verification
- PMID: 36502144
- PMCID: PMC9740536
- DOI: 10.3390/s22239444
AES Based White Box Cryptography in Digital Signature Verification
Abstract
According to the standard paradigm, white box cryptographic primitives are used to block black box attacks and protect sensitive information. This is performed to safeguard the protected information and keys against black box assaults. An adversary in such a setting is aware of the method and can analyze many system inputs and outputs, but is blind to the specifics of how a critical instantiation primitive is implemented. This is the focus of white-box solutions, which are designed to withstand attacks that come from the execution environment. This is significant because an attacker may obtain unrestricted access to the program's execution in this environment. The purpose of this article is to assess the efficiency of white-box implementations in terms of security. Our contribution is twofold: first, we explore the practical implementations of white-box approaches, and second, we analyze the theoretical foundations upon which these implementations are built. First, a research proposal is crafted that details white-box applications of DES and AES encryption algorithms. To begin, this preparation is necessary. The research effort planned for this project also includes cryptanalysis of these techniques. Once the general cryptanalysis results have been examined, the white-box design approaches will be covered. We have decided to launch an investigation into creating a theoretical model for white box, since no prior formal definitions have been offered, and suggested implementations have not been accompanied by any assurance of security. This is due to the fact that no formal definition of "white box" has ever been provided. In this way lies the explanation for why this is the situation. We define WBC to encompass the security requirements of WBC specified over a white box cryptography technology and a security concept by studying formal models of obfuscation and shown security. This definition is the product of extensive investigation. This state-of-the-art theoretical model provides a setting in which to investigate the security of white-box implementations, leading to a wide range of positive and negative conclusions. As a result, this paper includes the results of a Digital Signature Algorithm (DSA) study which may be put to use in the real world with signature verification. Possible future applications of White Box Cryptography (WBC) research findings are discussed in light of these purposes and areas of investigation.
Keywords: AES; attack; digital signature; white box cryptography.
Conflict of interest statement
The authors declare no conflict of interest.
Figures
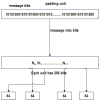
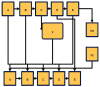
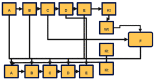
References
-
- Abdullah K., Bakar S.A., Kamis N.H., Aliamis H. RSAcryptosystem with Fuzzy Set Theory for Encryption and Decryption; Proceedings of the 13th IMT-GT International Conference on Mathematics, Statistics and their Applications (ICMSA2017); Kedah, Malaysia. 4–7 December 2017; pp. 1–6.
-
- Abu-Dawas M.A., Hussain A.K. Enhancement of RSA scheme using agreement secure information for nearest parameters. Int. J. Comput. Inf. Technol. 2015;4:194–196.
-
- Aiswarya P.M., Raj A.A., John D., Martin L., Sreenu G. Binary RSA encryption algorithm; Proceedings of the International Conference on Control, Instrumentation, Communication and Computational Technologies (ICCICCT); Thuckalay, India. 16–17 December 2016; pp. 178–181.
-
- Ali H., Al-Salami M. Timing attack prospect for RSA cryptanalysis using genetic algorithm technique. Int. Arab. J. Inf. Technol. 2004;1:80–84.
-
- Ali-Al-Mamun M., Islam M.M., Romman S.M., Salahuddin Ahmad A.H. Performance evaluation of several efficient RSA variants. Int. J. Comput. Sci. Netw. Secur. 2008;1:7–11.
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources
Other Literature Sources
Research Materials

