Combined Pseudo-Random Sequence Generator for Cybersecurity
- PMID: 36560068
- PMCID: PMC9785807
- DOI: 10.3390/s22249700
Combined Pseudo-Random Sequence Generator for Cybersecurity
Abstract
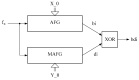
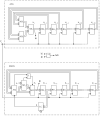
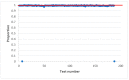
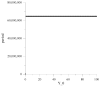
Random and pseudo-random number and bit sequence generators with a uniform distribution law are the most widespread and in demand in the market of pseudo-random generators. Depending on the specific field of application, the requirements for their implementation and the quality of the generator's output sequence change. In this article, we have optimized the structures of the classical additive Fibonacci generator and the modified additive Fibonacci generator when they work together. The ranges of initial settings of structural elements (seed) of these generators have been determined, which guarantee acceptable statistical characteristics of the output pseudo-random sequence, significantly expanding the scope of their possible application, including cybersecurity. When studying the statistical characteristics of the modified additive Fibonacci generator, it was found that they significantly depend on the signal from the output of the logic circuit entering the structure. It is proved that acceptable statistical characteristics of the modified additive Fibonacci generator, and the combined generator realized on its basis, are provided at odd values of the module of the recurrent equation describing the work of such generator. The output signal of the combined generator has acceptable characteristics for a wide range of values of the initial settings for the modified additive Fibonacci generator and the classic additive Fibonacci generator. Regarding the use of information security, it is worth noting the fact that for modern encryption and security programs, generators of random numbers and bit sequences and approaches to their construction are crucial and critical.
Keywords: authentication; encryption of information; pseudo-random number; pseudo-random sequence generators.
Conflict of interest statement
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
Figures

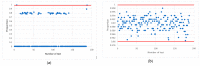
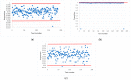


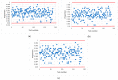
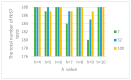


References
-
- Dichtl M., Golić J.D. Cryptographic Hardware and Embedded Systems—CHES 2007. Springer; Berlin/Heidelberg, Germany: 2007. High-Speed True Random Number Generation with Logic Gates Only; pp. 45–62. (Lecture Notes in Computer Science Book Series).
-
- Mandrona M.N., Maksymovych V.N. Comparative Analysis of Pseudorandom Bit Sequence Generators. J. Autom. Inf. Sci. 2017;49:78–86. doi: 10.1615/JAutomatInfScien.v49.i3.90. - DOI
-
- Fishman G.S. Discrete-Event Simulation. Springer; New York, NY, USA: 2001. Pseudorandom Number Generation; pp. 416–451. (Springer Series in Operations Research). - DOI
-
- François M., Defour D., Berthomé P. Theory and Applications of Models of Computation—TAMC 2014. Volume 8402. Springer; Cham, Switzerland: 2014. A Pseudo-Random Bit Generator Based on Three Chaotic Logistic Maps and IEEE 754-2008 Floating-Point Arithmetic. (Lecture Notes in Computer Science Book Series). - DOI
MeSH terms
LinkOut - more resources
Full Text Sources

