A Blockchain-Based Authentication and Authorization Scheme for Distributed Mobile Cloud Computing Services
- PMID: 36772304
- PMCID: PMC9921567
- DOI: 10.3390/s23031264
A Blockchain-Based Authentication and Authorization Scheme for Distributed Mobile Cloud Computing Services
Abstract
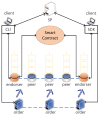
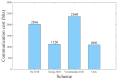
Authentication and authorization constitute the essential security component, access control, for preventing unauthorized access to cloud services in mobile cloud computing (MCC) environments. Traditional centralized access control models relying on third party trust face a critical challenge due to a high trust cost and single point of failure. Blockchain can achieve the distributed trust for access control designs in a mutual untrustworthy scenario, but it also leads to expensive storage overhead. Considering the above issues, this work constructed an authentication and authorization scheme based on blockchain that can provide a dynamic update of access permissions by utilizing the smart contract. Compared with the conventional authentication scheme, the proposed scheme integrates an extra authorization function without additional computation and communication costs in the authentication phase. To improve the storage efficiency and system scalability, only one transaction is required to be stored in blockchain to record a user's access privileges on different service providers (SPs). In addition, mobile users in the proposed scheme are able to register with an arbitrary SP once and then utilize the same credential to access different SPs with different access levels. The security analysis indicates that the proposed scheme is secure under the random oracle model. The performance analysis clearly shows that the proposed scheme possesses superior computation and communication efficiencies and requires a low blockchain storage capacity for accomplishing user registration and updates.
Keywords: access control; authentication; authorization; blockchain; mobile cloud computing.
Conflict of interest statement
The authors declare no conflict of interest.
Figures






Similar articles
-
An efficient blockchain-based authentication scheme with transferability.PLoS One. 2024 Sep 12;19(9):e0310094. doi: 10.1371/journal.pone.0310094. eCollection 2024. PLoS One. 2024. PMID: 39264886 Free PMC article.
-
A secure end-to-end communication framework for cooperative IoT networks using hybrid blockchain system.Sci Rep. 2025 Apr 1;15(1):11077. doi: 10.1038/s41598-025-96002-w. Sci Rep. 2025. PMID: 40169696 Free PMC article.
-
Zero trust in edge computing environment: a blockchain based practical scheme.Math Biosci Eng. 2022 Feb 18;19(4):4196-4216. doi: 10.3934/mbe.2022194. Math Biosci Eng. 2022. PMID: 35341294
-
Design of a Secure Medical Data Sharing Scheme Based on Blockchain.J Med Syst. 2020 Jan 8;44(2):52. doi: 10.1007/s10916-019-1468-1. J Med Syst. 2020. PMID: 31915982 Review.
-
A Comparative Analysis on Blockchain versus Centralized Authentication Architectures for IoT-Enabled Smart Devices in Smart Cities: A Comprehensive Review, Recent Advances, and Future Research Directions.Sensors (Basel). 2022 Jul 10;22(14):5168. doi: 10.3390/s22145168. Sensors (Basel). 2022. PMID: 35890848 Free PMC article. Review.
Cited by
-
Self-sovereign management scheme of personal health record with personal data store and decentralized identifier.Comput Struct Biotechnol J. 2024 Nov 28;28:16-28. doi: 10.1016/j.csbj.2024.11.036. eCollection 2025. Comput Struct Biotechnol J. 2024. PMID: 39868001 Free PMC article.
References
-
- Wang Y., Chen I.R., Wang D.C. A Survey of Mobile Cloud Computing Applications: Perspectives and Challenges. Wirel. Pers. Commun. 2015;80:1607–1623. doi: 10.1007/s11277-014-2102-7. - DOI
-
- Alizadeh M., Abolfazli S., Zamani M., Baharun S., Sakurai K. Authentication in mobile cloud computing: A survey. J. Netw. Comput. Appl. 2016;61:59–80. doi: 10.1016/j.jnca.2015.10.005. - DOI
-
- Odelu V., Das A.K., Kumari S., Huang X., Wazid M. Provably secure authenticated key agreement scheme for distributed mobile cloud computing services. Future Gener. Comput. Syst. 2017;68:74–88. doi: 10.1016/j.future.2016.09.009. - DOI
-
- Irshad A., Chaudhry S.A., Alomari O.A., Yahya K., Kumar N. A Novel Pairing-Free Lightweight Authentication Protocol for Mobile Cloud Computing Framework. IEEE Syst. J. 2021;15:3664–3672. doi: 10.1109/JSYST.2020.2998721. - DOI
-
- AlAhmad A.S., Kahtan H., Alzoubi Y.I., Ali O., Jaradat A. Mobile cloud computing models security issues: A systematic review. J. Netw. Comput. Appl. 2021;190:103152. doi: 10.1016/j.jnca.2021.103152. - DOI
Grants and funding
LinkOut - more resources
Full Text Sources

