A technology transfer journey to a model-driven access control system
- PMID: 36817285
- PMCID: PMC9913019
- DOI: 10.1007/s10009-023-00697-z
A technology transfer journey to a model-driven access control system
Abstract
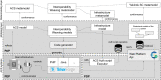
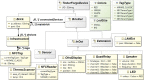
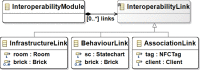
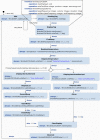
In the model-driven security domain, access control systems provide an application for handling access of persons through controlled gates. A gate, such as a door, can have a lock mechanism for securing the area from unauthorized access. Most commercial solutions for access control management offer pre-packaged software systems where customization of the authorization logic is either not allowed or subject to payment. Moreover, cross-platform development is a barrier for solution providers due to the high cost of development and maintenance that it implies. To overcome these limitations and further optimize the entire access control systems development process, we propose a model-driven approach that supports automatic code generation to enable communication between an IoT infrastructure and platforms for Facility Access Management. Specifically, the approach combines the benefits of Near-Field Communication (NFC) and Tinkerforge (i.e., an open-source hardware platform) with model-driven techniques. This allows the approach to exploit both behavioral and structural models for the modeling and the consequent code generation of part of the authorization mechanism, thus providing complete coverage of the code generated for the whole system. We implemented and evaluated our approach in a real-world case study within the premises of a fitness center with an IoT infrastructure consisting of several heterogeneous sensors by showing its practical applicability. Experimental results demonstrate the effectiveness of our approach in supporting abstraction and automation concerning traditional code-centric development through code generation features. Consequently, our approach makes the whole development process less time-consuming and error-prone, thus reducing the system's time to market.
Keywords: Access control system (ACS); IoT; MDE; Near-field communication (NFC).
© The Author(s) 2023.
Figures







References
-
- Moreno, M.V., Hernández, J.L., Skarmeta, A.F.: A new location-aware authorization mechanism for indoor environments. In: International Conference on Advanced Information Networking and Applications Workshops, pp. 791–796 (2014). IEEE
-
- Lúcio, L., Zhang, Q., Nguyen, P., Amrani, M., Klein, J., Vangheluwe, H., Le Traon, Y. (2014). Advances in Model-Driven Security 93, 103–152 10.1016/B978-0-12-800162-2.00003-8
-
- Nguyen PH, Kramer M, Klein J, Le Traon Y. An extensive systematic review on the model-driven development of secure systems. Inf. Softw. Technol. 2015;68:62–81. doi: 10.1016/j.infsof.2015.08.006. - DOI
-
- Coskun V, Ozdenizci B, Ok K. A survey on near field communication (nfc) technology. Wirel. Pers. Commun. 2013;71(3):2259–2294. doi: 10.1007/s11277-012-0935-5. - DOI
-
- Bravo, J., Hervas, R., Chavira, G., Nava, S.W., Villarreal, V.: From implicit to touching interaction: Rfid and nfc approaches. In: Conference on Human System Interactions, pp. 743–748 (2008)
LinkOut - more resources
Full Text Sources
