Intrusion Detection System for IoT: Analysis of PSD Robustness
- PMID: 36850950
- PMCID: PMC9959363
- DOI: 10.3390/s23042353
Intrusion Detection System for IoT: Analysis of PSD Robustness
Abstract
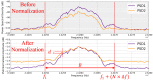
The security of internet of things (IoT) devices remains a major concern. These devices are very vulnerable because of some of their particularities (limited in both their memory and computing power, and available energy) that make it impossible to implement traditional security mechanisms. Consequently, researchers are looking for new security mechanisms adapted to these devices and the networks of which they are part. One of the most promising new approaches is fingerprinting, which aims to identify a given device by associating it with a unique signature built from its unique intrinsic characteristics, i.e., inherent imperfections, introduced by the manufacturing processes of its hardware. However, according to state-of-the-art studies, the main challenge that fingerprinting faces is the nonrelevance of the fingerprinting features extracted from hardware imperfections. Since these hardware imperfections can reflect on the RF signal for a wireless communicating device, in this study, we aim to investigate whether or not the power spectral density (PSD) of a device's RF signal could be a relevant feature for its fingerprinting, knowing that a relevant fingerprinting feature should remain stable regardless of the environmental conditions, over time and under influence of any other parameters. Through experiments, we were able to identify limits and possibilities of power spectral density (PSD) as a fingerprinting feature.
Keywords: device fingerprinting; device identification; internet of things (IoT); power spectral density (PSD); relevant fingerprinting feature.
Conflict of interest statement
The authors declare no conflict of interest.
Figures









References
-
- Kolias C., Kambourakis G., Stavrou A., Voas J. DDoS in the IoT: Mirai and Other Botnets. Computer. 2017;50:80–84. doi: 10.1109/MC.2017.201. - DOI
-
- Abbas S.G., Hashmat F., Shah G.A. A Multi-layer Industrial-IoT Attack Taxonomy: Layers, Dimensions, Techniques and Application; Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom); Guangzhou, China. 29 December 2020–1 January 2021; pp. 1820–1825. - DOI
-
- Khanam S., Ahmedy I.B., Idris M.Y.I., Jaward M.H., Bin Md Sabri A.Q. A Survey of Security Challenges, Attacks Taxonomy and Advanced Countermeasures in the Internet of Things. IEEE Access. 2020;8:219709–219743. doi: 10.1109/ACCESS.2020.3037359. - DOI
-
- Liang X., Kim Y. A Survey on Security Attacks and Solutions in the IoT Network; Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC); Virtual. 27 January 2021–30 January 2021; pp. 0853–0859. - DOI
-
- Mann P., Tyagi N., Gautam S., Rana A. Classification of Various Types of Attacks in IoT Environment; Proceedings of the 2020 12th International Conference on Computational Intelligence and Communication Networks (CICN); Bhimtal, India. 25–26 September 2020; pp. 346–350. - DOI
LinkOut - more resources
Full Text Sources

