Quantum asymmetric key crypto scheme using Grover iteration
- PMID: 36882516
- PMCID: PMC9992374
- DOI: 10.1038/s41598-023-30860-0
Quantum asymmetric key crypto scheme using Grover iteration
Abstract
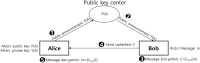
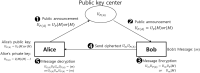
Here, we propose a quantum asymmetric key cryptography scheme using Grover's quantum search algorithm. In the proposed scheme, Alice generates a pair of public and private keys, keeps the private keys safe, and only discloses public keys to the outside. Bob uses Alice's public key to send a secret message to Alice and Alice uses her private key to decrypt the secret message. Furthermore, we discuss the safety of quantum asymmetric key encryption techniques based on quantum mechanical properties.
© 2023. The Author(s).
Conflict of interest statement
The authors declare no competing interests.
Figures
References
-
- Menezes, A. J., Paul, C., Van, O., & Scott A. Vanstone. Handbook of Applied Cryptography. (CRC press, Boca Raton, 1996)
-
- Forouzan, B. A., & Mukhopadhyay, D. Cryptography And Network Security (Sie). (McGraw-Hill Education, Noida, 2011).
-
- Stallings, W. & Tahiliani, M. P. (2014). Cryptography and network security: principles and practice, vol 6. Editor: Pearson London.
-
- Nielsen, M. A., & Chuang, I. Quantum Computation and Quantum Information. (American Association of Physics Teachers, College Park, 2002), pp. 558–559.
-
- Bennett, C. H. & Brassard, G. Quantum cryptography: Public key distribution and coin tossing. In Proc. of IEEE International Conf. on Computers, Systems and Signal Processing, vol 175. p. 8. (NY, 1984).
LinkOut - more resources
Full Text Sources

