Secured and Privacy-Preserving Multi-Authority Access Control System for Cloud-Based Healthcare Data Sharing
- PMID: 36904822
- PMCID: PMC10007450
- DOI: 10.3390/s23052617
Secured and Privacy-Preserving Multi-Authority Access Control System for Cloud-Based Healthcare Data Sharing
Abstract
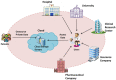
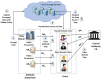
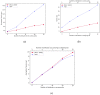
With continuous advancements in Internet technology and the increased use of cryptographic techniques, the cloud has become the obvious choice for data sharing. Generally, the data are outsourced to cloud storage servers in encrypted form. Access control methods can be used on encrypted outsourced data to facilitate and regulate access. Multi-authority attribute-based encryption is a propitious technique to control who can access encrypted data in inter-domain applications such as sharing data between organizations, sharing data in healthcare, etc. The data owner may require the flexibility to share the data with known and unknown users. The known or closed-domain users may be internal employees of the organization, and unknown or open-domain users may be outside agencies, third-party users, etc. In the case of closed-domain users, the data owner becomes the key issuing authority, and in the case of open-domain users, various established attribute authorities perform the task of key issuance. Privacy preservation is also a crucial requirement in cloud-based data-sharing systems. This work proposes the SP-MAACS scheme, a secure and privacy-preserving multi-authority access control system for cloud-based healthcare data sharing. Both open and closed domain users are considered, and policy privacy is ensured by only disclosing the names of policy attributes. The values of the attributes are kept hidden. Characteristic comparison with similar existing schemes shows that our scheme simultaneously provides features such as multi-authority setting, expressive and flexible access policy structure, privacy preservation, and scalability. The performance analysis carried out by us shows that the decryption cost is reasonable enough. Furthermore, the scheme is demonstrated to be adaptively secure under the standard model.
Keywords: access control; attribute-based encryption; cloud storage; electronic health records; multiple authorities; privacy preservation.
Conflict of interest statement
The authors declare no conflict of interest.
Figures
References
-
- Kanwal T., Anjum A., Khan A. Privacy preservation in e-health cloud: Taxonomy, privacy requirements, feasibility analysis, and opportunities. Clust. Comput. 2021;24:293–317. doi: 10.1007/s10586-020-03106-1. - DOI
-
- Goyal V., Pandey O., Sahai A., Waters B. Attribute-based encryption for fine-grained access control of encrypted data; Proceedings of the 13th ACM Conference on Computer and Communications Security; Alexandria, VA, USA. 30 October–3 November 2006; pp. 89–98.
-
- Bethencourt J., Sahai A., Waters B. Ciphertext-policy attribute-based encryption; Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07); Berkeley, CA, USA. 20–23 May 2007; pp. 321–334. - DOI
-
- Hur J. Improving security and efficiency in attribute-based data sharing. IEEE Trans. Knowl. Data Eng. 2011;25:2271–2282. doi: 10.1109/TKDE.2011.78. - DOI
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources