A Decade of Reoccurring Software Weaknesses
- PMID: 36936247
- PMCID: PMC10021008
- DOI: 10.1109/msec.2021.3082757
A Decade of Reoccurring Software Weaknesses
Abstract
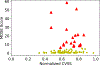
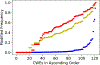
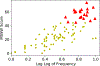
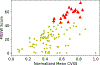
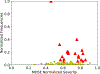
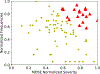
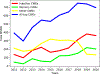
The Common Weakness Enumeration (CWE) community publishes an aggregate metric to calculate the 'Most Dangerous Software Errors.' However, the used equation highly biases frequency over exploitability and impact. We provide a metric to mitigate this bias and discuss the most significant software weaknesses over the last ten years.
Figures


References
-
- NIST, “National vulnerability database,” 2020, accessed: 2020–01–10. [Online]. Available: https://nvd.nist.gov
-
- MITRE, “Common weakness enumeration,” 2019, accessed: 2019–12–10. [Online]. Available: https://cwe.mitre.org
-
- MITRE, “2019 cwe top 25 most dangerous software errors,” 2020, accessed: 2020–02–01. [Online]. Available: https://cwe.mitre.org/top25/archive/2019/2019_cwe_top25.html
-
- Galhardo CC, Mell P, Bojanova I, and Gueye A, “Measurements of the most significant software security weaknesses,” in Annual Computer Security Applications Conference (ACSAC), 2020, pp. 154–164
-
- Ross Ronald S., “Guide for conducting risk assessments,” 2012, accessed: 2020–01–10. [Online]. Available: https://www.nist.gov/publications/guide-conducting-risk-assessments
Grants and funding
LinkOut - more resources
Full Text Sources
