An Intelligent Healthcare System Using IoT in Wireless Sensor Network
- PMID: 37299782
- PMCID: PMC10255690
- DOI: 10.3390/s23115055
An Intelligent Healthcare System Using IoT in Wireless Sensor Network
Abstract
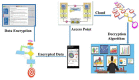
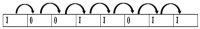
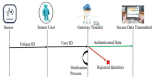
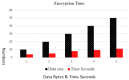
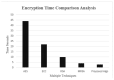
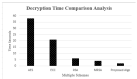
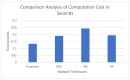
The Internet of Things (IoT) uses wireless networks without infrastructure to install a huge number of wireless sensors that track system, physical, and environmental factors. There are a variety of WSN uses, and some well-known application factors include energy consumption and lifespan duration for routing purposes. The sensors have detecting, processing, and communication capabilities. In this paper, an intelligent healthcare system is proposed which consists of nano sensors that collect real-time health status and transfer it to the doctor's server. Time consumption and various attacks are major concerns, and some existing techniques contain stumbling blocks. Therefore, in this research, a genetic-based encryption method is advocated to protect data transmitted over a wireless channel using sensors to avoid an uncomfortable data transmission environment. An authentication procedure is also proposed for legitimate users to access the data channel. Results show that the proposed algorithm is lightweight and energy efficient, and time consumption is 90% lower with a higher security ratio.
Keywords: IoT; authentication; cryptography; genetic algorithm; intelligent healthcare; remote patients monitoring system; wireless sensor networks.
Conflict of interest statement
The authors declare no conflict of interest.
Figures



References
-
- Akyildiz I.F., Su W., Subramaniam Y.S., Cayirci E. Wireless sensor networks: A survey. Comput. Netw. 2002;38:393–422. doi: 10.1016/S1389-1286(01)00302-4. - DOI
-
- Estrin D., Culler D., Pister K., Sukhatme G. Connecting the physical world with pervasive networks. IEEE Pervasive Comput. 2002;7:59–69. doi: 10.1109/MPRV.2002.993145. - DOI
-
- Akyildiz I., Jornet F. Electromagnetic wireless nano sensor networks. Nano Commun. Netw. 2010;1:3–19. doi: 10.1016/j.nancom.2010.04.001. - DOI
-
- Akyildiz I., Kasimoglu F. Wireless sensor and actor networks: Research challenges. Ad Hoc Netw. 2014;2:351–367. doi: 10.1016/j.adhoc.2004.04.003. - DOI
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources

