Demonstration of quantum-digital payments
- PMID: 37386044
- PMCID: PMC10310712
- DOI: 10.1038/s41467-023-39519-w
Demonstration of quantum-digital payments
Erratum in
-
Author Correction: Demonstration of quantum-digital payments.Nat Commun. 2023 Aug 21;14(1):5059. doi: 10.1038/s41467-023-40866-x. Nat Commun. 2023. PMID: 37604807 Free PMC article. No abstract available.
Abstract
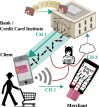
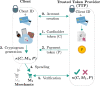
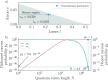
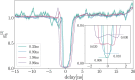
Digital payments have replaced physical banknotes in many aspects of our daily lives. Similarly to banknotes, they should be easy to use, unique, tamper-resistant and untraceable, but additionally withstand digital attackers and data breaches. Current technology substitutes customers' sensitive data by randomized tokens, and secures the payment's uniqueness with a cryptographic function, called a cryptogram. However, computationally powerful attacks violate the security of these functions. Quantum technology comes with the potential to protect even against infinite computational power. Here, we show how quantum light can secure daily digital payments by generating inherently unforgeable quantum cryptograms. We implement the scheme over an urban optical fiber link, and show its robustness to noise and loss-dependent attacks. Unlike previously proposed protocols, our solution does not depend on long-term quantum storage or trusted agents and authenticated channels. It is practical with near-term technology and may herald an era of quantum-enabled security.
© 2023. The Author(s).
Conflict of interest statement
P.W., M.B., T.G., E.S., and P.S. are employees of the University of Vienna, which has applied for a patent (EP 23168897.9) for the use of a quantum payment token scheme with P.W., M.B., T.G., E.S., and P.S. listed as inventors. The remaining authors declare no competing interests.
Figures

References
-
- Martín-López E, et al. Experimental realization of shor’s quantum factoring algorithm using qubit recycling. Nat. Photon. 2012;6:773–776. doi: 10.1038/nphoton.2012.259. - DOI
-
- Shor PW. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 1997;26:1484–1509. doi: 10.1137/S0097539795293172. - DOI
-
- Beullens, W. Breaking rainbow takes a weekend on a laptop. Cryptology ePrint Archive, Paper 2022/214 (2022). https://eprint.iacr.org/2022/214.
-
- Castryck, W. & Decru, T. An efficient key recovery attack on sidh (preliminary version). Cryptology ePrint Archive, Paper 2022/975 (2022). https://eprint.iacr.org/2022/975.
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources

