Plant and Salamander Inspired Network Attack Detection and Data Recovery Model
- PMID: 37420729
- PMCID: PMC10302505
- DOI: 10.3390/s23125562
Plant and Salamander Inspired Network Attack Detection and Data Recovery Model
Abstract
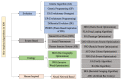
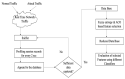
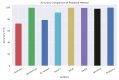
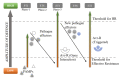
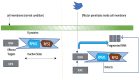
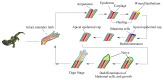
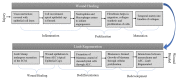
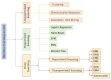
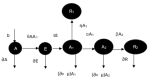
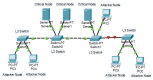
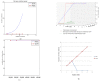
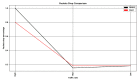
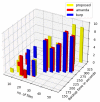
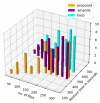
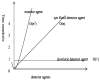
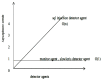
The number of users of the Internet has been continuously rising, with an estimated 5.1 billion users in 2023, which comprises around 64.7% of the total world population. This indicates the rise of more connected devices to the network. On average, 30,000 websites are hacked daily, and nearly 64% of companies worldwide experience at least one type of cyberattack. As per IDC's 2022 Ransomware study, two-thirds of global organizations were hit by a ransomware attack that year. This creates the desire for a more robust and evolutionary attack detection and recovery model. One aspect of the study is the bio-inspiration models. This is because of the natural ability of living organisms to withstand various odd circumstances and overcome them with an optimization strategy. In contrast to the limitations of machine learning models with the need for quality datasets and computational availability, bio-inspired models can perform in low computational environments, and their performances are designed to evolve naturally with time. This study concentrates on exploring the evolutionary defence mechanism in plants and understanding how plants react to any known external attacks and how the response mechanism changes to unknown attacks. This study also explores how regenerative models, such as salamander limb regeneration, could build a network recovery system where services could be automatically activated after a network attack, and data could be recovered automatically by the network after a ransomware-like attack. The performance of the proposed model is compared to open-source IDS Snort and data recovery systems such as Burp and Casandra.
Keywords: bio-inspired algorithm; evolutionary computing; intrusion detection; network security; ransomware.
Conflict of interest statement
The authors declare no conflict of interest.
Figures

References
-
- Demertzis K., Iliadis L. Computation, Cryptography, and Network Security. Springer; Berlin/Heidelberg, Germany: 2015. A bio-inspired hybrid artificial intelligence framework for cybersecurity; pp. 161–193.
-
- Thakkar A., Lohiya R. Swarm and Evolutionary Computation. Elseiver; Amsterdam, The Netherlands: 2019. Role of Swarm and evolutionary algorithms for intrusion detection system: A survey.
-
- Chen Y., Abraham A., Yang B. Hybrid flexible neural- tree-based intrusion detection systems. Int. J. Intell. Syst. 2007;22:337–352. doi: 10.1002/int.20203. - DOI
-
- Neelima D., Karthik J., Aravind John K., Gowthami S., Nayak J. Soft Computing in Data Analytics. Springer; Singapore: 2019. Soft Computing-Based Intrusion Detection Approaches: An Analytical Study; pp. 635–651.
MeSH terms
LinkOut - more resources
Full Text Sources
Research Materials

