Trust based attachment
- PMID: 37610996
- PMCID: PMC10446209
- DOI: 10.1371/journal.pone.0288142
Trust based attachment
Abstract
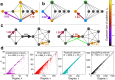
In social systems subject to indirect reciprocity, a positive reputation is key for increasing one's likelihood of future positive interactions [1-13]. The flow of gossip can amplify the impact of a person's actions on their reputation depending on how widely it spreads across the social network, which leads to a percolation problem [14]. To quantify this notion, we calculate the expected number of individuals, the "audience", who find out about a particular interaction. For a potential donor, a larger audience constitutes higher reputational stakes, and thus a higher incentive, to perform "good" actions in line with current social norms [7, 15]. For a receiver, a larger audience therefore increases the trust that the partner will be cooperative. This idea can be used for an algorithm that generates social networks, which we call trust based attachment (TBA). TBA produces graphs that share crucial quantitative properties with real-world networks, such as high clustering, small-world behavior, and powerlaw degree distributions [16-21]. We also show that TBA can be approximated by simple friend-of-friend routines based on triadic closure, which are known to be highly effective at generating realistic social network structures [19, 22-25]. Therefore, our work provides a new justification for triadic closure in social contexts based on notions of trust, gossip, and social information spread. These factors are thus identified as potential significant influences on how humans form social ties.
Copyright: © 2023 Kates-Harbeck, Nowak. This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Conflict of interest statement
The authors have declared that no competing interests exist.
Figures



References
-
- Alexander R. The biology of moral systems (foundations of human behavior). 1987;.
Publication types
MeSH terms
LinkOut - more resources
Full Text Sources
Miscellaneous

