Multiple modes of data sharing can facilitate secondary use of sensitive health data for research
- PMID: 37802544
- PMCID: PMC10565310
- DOI: 10.1136/bmjgh-2023-013092
Multiple modes of data sharing can facilitate secondary use of sensitive health data for research
Abstract
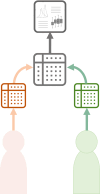
Evidence-based healthcare relies on health data from diverse sources to inform decision-making across different domains, including disease prevention, aetiology, diagnostics, therapeutics and prognosis. Increasing volumes of highly granular data provide opportunities to leverage the evidence base, with growing recognition that health data are highly sensitive and onward research use may create privacy issues for individuals providing data. Concerns are heightened for data without explicit informed consent for secondary research use. Additionally, researchers-especially from under-resourced environments and the global South-may wish to participate in onward analysis of resources they collected or retain oversight of onward use to ensure ethical constraints are respected. Different data-sharing approaches may be adopted according to data sensitivity and secondary use restrictions, moving beyond the traditional Open Access model of unidirectional data transfer from generator to secondary user. We describe collaborative data sharing, facilitating research by combining datasets and undertaking meta-analysis involving collaborating partners; federated data analysis, where partners undertake synchronous, harmonised analyses on their independent datasets and then combine their results in a coauthored report, and trusted research environments where data are analysed in a controlled environment and only aggregate results are exported. We review how deidentification and anonymisation methods, including data perturbation, can reduce risks specifically associated with health data secondary use. In addition, we present an innovative modularised approach for building data sharing agreements incorporating a more nuanced approach to data sharing to protect privacy, and provide a framework for building the agreements for each of these data-sharing scenarios.
Keywords: Health policies and all other topics; Public Health.
© Author(s) (or their employer(s)) 2023. Re-use permitted under CC BY-NC. No commercial re-use. See rights and permissions. Published by BMJ.
Conflict of interest statement
Competing interests: None declared.
Figures



References
-
- Afraid of Scooping – Case Study on Researcher Strategies against Fear of Scooping in the Context of Open Science. [27-Apr-2018]. https://datascience.codata.org/articles/10.5334/dsj-2017-029/ Available. Accessed. - DOI
Publication types
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources
