The Index of Intrusion Control (IIC): Capturing individual variability in intentional intrusion control in the laboratory
- PMID: 38291222
- PMCID: PMC11133188
- DOI: 10.3758/s13428-024-02345-z
The Index of Intrusion Control (IIC): Capturing individual variability in intentional intrusion control in the laboratory
Abstract
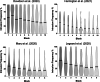
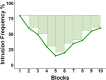
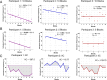
Intrusive memories can be downregulated using intentional memory control, as measured via the Think/No-Think paradigm. In this task, participants retrieve or suppress memories in response to an associated reminder cue. After each suppression trial, participants rate whether the association intruded into awareness. Previous research has found that repeatedly exerting intentional control over memory intrusions reduces their frequency. This decrease is often summarised with a linear index, which may miss more complex patterns characterising the temporal dynamics of intrusion control. The goal of this paper is to propose a novel metric of intrusion control that captures those dynamic changes over time as a single index. Results from a mega-analysis of published datasets revealed that the change in intrusion frequencies across time is not purely linear, but also includes non-linear dynamics that seem best captured by a log function of the number of suppression attempts. To capture those linear and non-linear dynamics, we propose the Index of Intrusion Control (IIC), which relies on the integral of intrusion changes across suppression attempts. Simulations revealed that the IIC best captured the linear and non-linear dynamics of intrusion suppression when compared with other linear or non-linear indexes of control, such as the regression slope or Spearman correlation, respectively. Our findings demonstrate how the IIC may therefore act as a more reliable metric to capture individual differences in intrusion control, and examine the role of non-linear dynamics characterizing the conscious access to unwanted memories.
Keywords: Index of Intrusion Control (IIC); Intentional memory control; Intrusions; Think/No-Think task.
© 2024. The Author(s).
Conflict of interest statement
The authors declare no competing interests.
Figures

Similar articles
-
Successfully controlling intrusive memories is harder when control must be sustained.Memory. 2017 Oct;25(9):1201-1216. doi: 10.1080/09658211.2017.1282518. Epub 2017 Feb 21. Memory. 2017. PMID: 28276978 Free PMC article.
-
Tracking the intrusion of unwanted memories into awareness with event-related potentials.Neuropsychologia. 2016 Aug;89:510-523. doi: 10.1016/j.neuropsychologia.2016.07.008. Epub 2016 Jul 7. Neuropsychologia. 2016. PMID: 27396675 Free PMC article.
-
It's all in the detail: intentional forgetting of autobiographical memories using the autobiographical think/no-think task.J Exp Psychol Learn Mem Cogn. 2013 Mar;39(2):375-93. doi: 10.1037/a0028888. Epub 2012 Jun 11. J Exp Psychol Learn Mem Cogn. 2013. PMID: 22686849
-
Individual differences in the suppression of unwanted memories: the executive deficit hypothesis.Acta Psychol (Amst). 2008 Mar;127(3):623-35. doi: 10.1016/j.actpsy.2007.12.004. Epub 2008 Feb 1. Acta Psychol (Amst). 2008. PMID: 18242571 Review.
-
[Episodic autobiographical memory in depression: a review].Encephale. 2006 Oct;32(5 Pt 1):781-8. doi: 10.1016/s0013-7006(06)76231-5. Encephale. 2006. PMID: 17099603 Review. French.
Cited by
-
A mindful approach to controlling intrusive thoughts.Sci Rep. 2023 Jul 6;13(1):10966. doi: 10.1038/s41598-023-37447-9. Sci Rep. 2023. PMID: 37414828 Free PMC article.
References
Publication types
MeSH terms
LinkOut - more resources
Full Text Sources

