Linking QKD Testbeds across Europe
- PMID: 38392378
- PMCID: PMC10888270
- DOI: 10.3390/e26020123
Linking QKD Testbeds across Europe
Abstract
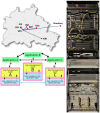
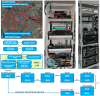
Quantum-key-distribution (QKD) networks are gaining importance and it has become necessary to analyze the most appropriate methods for their long-distance interconnection. In this paper, four different methods of interconnecting remote QKD networks are proposed. The methods are used to link three different QKD testbeds in Europe, located in Berlin, Madrid, and Poznan. Although long-distance QKD links are only emulated, the methods used can serve as a blueprint for the secure interconnection of distant QKD networks in the future. Specifically, the presented approaches combine, in a transparent way, different fiber and satellite physical media, as well as common standards of key delivery interfaces. The testbed interconnections are designed to increase the security by utilizing multipath techniques and multiple hybridizations of QKD and post-quantum cryptography (PQC) algorithms.
Keywords: QKD; quantum communications; quantum cryptography; quantum networks.
Conflict of interest statement
Authors Max Brauer, Ralf-Peter Braun, Marc Geitz were employed by the company T-Labs, Deutsche Telekom AG. Authors Hans H. Brunner, Fred Fung, Momtchil Peev were employed by the company Munich Research Center, Huawei Technologies Duesseldorf GmbH. Authors Antonio Pastor and Diego R. Lopez were employed by the company Telefónica gCTIO/I+D. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Figures





References
-
- Shor P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999;41:303–332. doi: 10.1137/S0036144598347011. - DOI
-
- Moody D. Let’s Get Ready to Rumble. The NIST PQC “Competition”; Proceedings of the First PQC Standardization Conference; Fort Lauderdale, FL, USA. 12–13 April 2018; pp. 11–13.
-
- NIST, Information Technology Laboratory, C.S.R.C. Post Quantum Cryptography, Draft FIPS 203, FIPS 204 and FIPS 205, Which Specify Algorithms Derived from CRYSTALS-Dilithium, CRYSTALS-KYBER and SPHINCS+ [(accessed on 8 November 2023)];2023 Available online: https://csrc.nist.gov/projects/post-quantum-cryptography.
-
- Braun R.P., Geitz M. The OpenQKD Testbed in Berlin; Proceedings of the 2021 Asia Communications and Photonics Conference (ACP); Shanghai, China. 24–27 October 2021; pp. 1–3.
-
- Rydlichkowski P. OPENQKD project Work Package 7 review; Proceedings of the QKD Days; Madrid, Spanish. 13 December 2022.
LinkOut - more resources
Full Text Sources

