Cryptographic approaches to authenticating synthetic DNA sequences
- PMID: 38418329
- PMCID: PMC11309913
- DOI: 10.1016/j.tibtech.2024.02.002
Cryptographic approaches to authenticating synthetic DNA sequences
Abstract
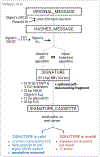
In a bioeconomy that relies on synthetic DNA sequences, the ability to ensure their authenticity is critical. DNA watermarks can encode identifying data in short sequences and can be combined with error correction and encryption protocols to ensure that sequences are robust to errors and securely communicated. New digital signature techniques allow for public verification that a sequence has not been modified and can contain sufficient information for synthetic DNA to be self-documenting. In translating these techniques from bacteria to more complex genetically modified organisms (GMOs), special considerations must be made to allow for public verification of these products. We argue that these approaches should be widely implemented to assert authorship, increase the traceability, and detect the unauthorized use of synthetic DNA.
Keywords: DNA cryptography; DNA watermark; cyberbiosecurity; digital signature; genetic engineering attribution.
Copyright © 2024 The Author(s). Published by Elsevier Ltd.. All rights reserved.
Conflict of interest statement
Declaration of interests J.P. and S.P. have financial interests in GenoFAB, Inc. This company may benefit or be perceived as benefiting from this publication.
Figures



Similar articles
-
Prescription of Controlled Substances: Benefits and Risks.2025 Jul 6. In: StatPearls [Internet]. Treasure Island (FL): StatPearls Publishing; 2025 Jan–. 2025 Jul 6. In: StatPearls [Internet]. Treasure Island (FL): StatPearls Publishing; 2025 Jan–. PMID: 30726003 Free Books & Documents.
-
High-throughput library transgenesis in Caenorhabditis elegans via Transgenic Arrays Resulting in Diversity of Integrated Sequences (TARDIS).Elife. 2023 Jul 4;12:RP84831. doi: 10.7554/eLife.84831. Elife. 2023. PMID: 37401921 Free PMC article.
-
Management of urinary stones by experts in stone disease (ESD 2025).Arch Ital Urol Androl. 2025 Jun 30;97(2):14085. doi: 10.4081/aiua.2025.14085. Epub 2025 Jun 30. Arch Ital Urol Androl. 2025. PMID: 40583613 Review.
-
Can a Liquid Biopsy Detect Circulating Tumor DNA With Low-passage Whole-genome Sequencing in Patients With a Sarcoma? A Pilot Evaluation.Clin Orthop Relat Res. 2025 Jan 1;483(1):39-48. doi: 10.1097/CORR.0000000000003161. Epub 2024 Jun 21. Clin Orthop Relat Res. 2025. PMID: 38905450
-
The Black Book of Psychotropic Dosing and Monitoring.Psychopharmacol Bull. 2024 Jul 8;54(3):8-59. Psychopharmacol Bull. 2024. PMID: 38993656 Free PMC article. Review.
Cited by
-
Sequencing Strategy to Ensure Accurate Plasmid Assembly.bioRxiv [Preprint]. 2024 Jun 10:2024.03.25.586694. doi: 10.1101/2024.03.25.586694. bioRxiv. 2024. Update in: ACS Synth Biol. 2024 Dec 20;13(12):4099-4109. doi: 10.1021/acssynbio.4c00539. PMID: 38585828 Free PMC article. Updated. Preprint.
-
Self-documenting plasmids.Trends Biotechnol. 2025 Apr 7:S0167-7799(25)00095-2. doi: 10.1016/j.tibtech.2025.03.010. Online ahead of print. Trends Biotechnol. 2025. PMID: 40340197
-
Cyber-biological convergence: a systematic review and future outlook.Front Bioeng Biotechnol. 2024 Sep 24;12:1456354. doi: 10.3389/fbioe.2024.1456354. eCollection 2024. Front Bioeng Biotechnol. 2024. PMID: 39380896 Free PMC article.
-
Synsor: a tool for alignment-free detection of engineered DNA sequences.Front Bioeng Biotechnol. 2024 Jul 12;12:1375626. doi: 10.3389/fbioe.2024.1375626. eCollection 2024. Front Bioeng Biotechnol. 2024. PMID: 39070163 Free PMC article.
-
Engineering biology applications for environmental solutions: potential and challenges.Nat Commun. 2025 Apr 14;16(1):3538. doi: 10.1038/s41467-025-58492-0. Nat Commun. 2025. PMID: 40229265 Free PMC article. Review.
References
-
- Peccoud J et al. (2018) Cyberbiosecurity: from naive trust to risk awareness. Trends in biotechnology 36, 4–7 - PubMed
Publication types
MeSH terms
Substances
Grants and funding
LinkOut - more resources
Full Text Sources

