A federated authentication schema among multiple identity providers
- PMID: 38590890
- PMCID: PMC10999912
- DOI: 10.1016/j.heliyon.2024.e28560
A federated authentication schema among multiple identity providers
Abstract
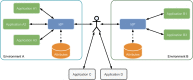
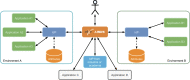
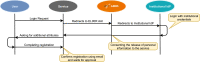
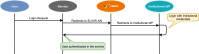
Single Sign-On (SSO) methods are the primary solution to authenticate users across multiple web systems. These mechanisms streamline the authentication procedure by avoiding duplicate developments of authentication modules for each application. Besides, these mechanisms also provide convenience to the end-user by keeping the user authenticated when switching between different contexts. To ensure this cross-application authentication, SSO relies on an Identity Provider (IdP), which is commonly set up and managed by each institution that needs to enforce SSO internally. However, the solution is not so straightforward when several institutions need to cooperate in a unique ecosystem. This could be tackled by centralizing the authentication mechanisms in one of the involved entities, a solution raising responsibilities that may be difficult for peers to accept. Moreover, this solution is not appropriate for dynamic groups, where peers may join or leave frequently. In this paper, we propose an architecture that uses a trusted third-party service to authenticate multiple entities, ensuring the isolation of the user's attributes between this service and the institutional SSO systems. This architecture was validated in the EHDEN Portal, which includes web tools and services of this European health project, to establish a Federated Authentication schema.
Keywords: ELIXIR AAI; Federated authentication; IdP; OAuth 2.0; SSO.
© 2024 The Author(s).
Conflict of interest statement
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Figures
References
-
- Wilson Y., Hingnikar A. Solving Identity Management in Modern Applications. Springer; 2019. Single sign-on; pp. 151–157. - DOI
-
- Hu J., Sun Q., Chen H. 2010 3rd IEEE International Conference on Broadband Network and Multimedia Technology (IC-BNMT) IEEE; 2010. Application of single sign-on (SSO) in digital campus; pp. 725–727.
-
- Bhosale S.K. 2008. Architecture of a Single Sign on (SSO) for Internet Banking.
-
- Radha V., Reddy D.H. A survey on single sign-on techniques. Proc. Technol. 2012;4:134–139.
-
- Armando A., Carbone R., Compagna L., Cuellar J., Tobarra L. Proceedings of the 6th ACM Workshop on Formal Methods in Security Engineering. 2008. Formal analysis of SAML 2.0 web browser single sign-on: breaking the SAML-based single sign-on for Google apps; pp. 1–10.
LinkOut - more resources
Full Text Sources

