A blended framework for audio spoof detection with sequential models and bags of auditory bites
- PMID: 39215070
- PMCID: PMC11364551
- DOI: 10.1038/s41598-024-71026-w
A blended framework for audio spoof detection with sequential models and bags of auditory bites
Abstract
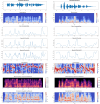
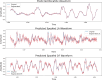
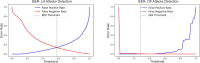
An automated speaker verification system uses the process of speech recognition to verify the identity of a user and block illicit access. Logical access attacks are efforts to obtain access to a system by tampering with its algorithms or data, or by circumventing security mechanisms. DeepFake attacks are a form of logical access threats that employs artificial intelligence to produce highly realistic audio clips of human voice, that may be used to circumvent vocal authentication systems. This paper presents a framework for the detection of Logical Access and DeepFake audio spoofings by integrating audio file components and time-frequency representation spectrograms into a lower-dimensional space using sequential prediction models. Bidirectional-LSTM trained on the bonafide class generates significant one-dimensional features for both classes. The feature set is then standardized to a fixed set using a novel Bags of Auditory Bites (BoAB) feature standardizing algorithm. The Extreme Learning Machine maps the feature space to predictions that differentiate between genuine and spoofed speeches. The framework is evaluated using the ASVspoof 2021 dataset, a comprehensive collection of audio recordings designed for evaluating the strength of speaker verification systems against spoofing attacks. It achieves favorable results on synthesized DeepFake attacks with an Equal Error Rate (EER) of 1.18% in the most optimal setting. Logical Access attacks were more challenging to detect at an EER of 12.22%. Compared to the state-of-the-arts in the ASVspoof2021 dataset, the proposed method notably improves EER for DeepFake attacks by an improvement rate of 95.16%.
© 2024. The Author(s).
Conflict of interest statement
The authors declare no competing interests.
Figures





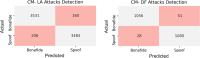
References
-
- Uludag, U. et al. Biometric cryptosystems: Issues and challenges. Proc. IEEE92, 948–960 (2004).10.1109/JPROC.2004.827372 - DOI
-
- Wells, A. & Usman, A. B. Privacy and biometrics for smart healthcare systems: Attacks, and techniques. Inf. Secur. J. Glob. Perspective. 33,1–25 (2023).
-
- Panda, R., Malheiro, R. M. & Paiva, R. P. Audio features for music emotion recognition: A survey. IEEE Trans. Affect. Comput.14, 68–88 (2020).10.1109/TAFFC.2020.3032373 - DOI
-
- Goode, Alan. Biometrics for banking: Best practices and barriers to adoption. Biom. Technol. Today2018(10), 5–7. 10.1016/S0969-4765(18)30156-5 (2018).10.1016/S0969-4765(18)30156-5 - DOI
-
- Herzberg, A. Payments and banking with mobile personal devices. Commun. ACM46(5), 53–58. 10.1145/769800.769801 (2003).10.1145/769800.769801 - DOI
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources

