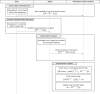
An efficient blockchain-based authentication scheme with transferability
- PMID: 39264886
- PMCID: PMC11392242
- DOI: 10.1371/journal.pone.0310094
An efficient blockchain-based authentication scheme with transferability
Abstract
In the development of web applications, the rapid advancement of Internet technologies has brought unprecedented opportunities and increased the demand for user authentication schemes. Before the emergence of blockchain technology, establishing trust between two unfamiliar entities relied on a trusted third party for identity verification. However, the failure or malicious behavior of such a trusted third party could undermine such authentication schemes (e.g., single points of failure, credential leaks). A secure authorization system is another requirement of user authentication schemes, as users must authorize other entities to act on their behalf in some situations. If the transfer of authentication permissions is not adequately restricted, security risks such as unauthorized transfer of permissions to entities may occur. Some research has proposed blockchain-based decentralized user authentication solutions to address these risks and enhance availability and auditability. However, as we know, most proposed schemes that allow users to transfer authentication permissions to other entities require significant gas consumption when deployed and triggered in smart contracts. To address this issue, we proposed an authentication scheme with transferability solely based on hash functions. By combining one-time passwords with Hashcash, the scheme can limit the number of times permissions can be transferred while ensuring security. Furthermore, due to its reliance solely on hash functions, our proposed authentication scheme has an absolute advantage regarding computational complexity and gas consumption in smart contracts. Additionally, we have deployed smart contracts on the Goerli test network and demonstrated the practicality and efficiency of this authentication scheme.
Copyright: © 2024 Jin, Omote. This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Conflict of interest statement
The authors have declared that no competing interests exist.
Figures
References
-
- Goldwasser S., Kalai Y. T., and Rothblum G. N., “One-time programs.,” in Crypto, vol. 5157, pp. 39–56, Springer, 2008.
-
- K. Durnoga, S. Dziembowski, T. Kazana, and M. Zajac, “One-time programs with limited memory,” in Information Security and Cryptology: 9th International Conference, Inscrypt 2013, Guangzhou, China, November 27-30, 2013, Revised Selected Papers, pp. 377–394, Springer, 2014.
-
- Li S., Xu C., Zhang Y., and Zhou J., “A secure two-factor authentication scheme from password-protected hardware tokens,” IEEE Transactions on Information Forensics and Security, vol. 17, pp. 3525–3538, 2022. doi: 10.1109/TIFS.2022.3209886 - DOI
-
- Mall P., Amin R., Das A. K., Leung M. T., and Choo K.-K. R., “PUF-based authentication and key agreement protocols for IoT, WSNs, and Smart Grids: a comprehensive survey,” IEEE Internet of Things Journal, vol. 9, no. 11, pp. 8205–8228, 2022. doi: 10.1109/JIOT.2022.3142084 - DOI
-
- Poettering B. and Stebila D., “Double-authentication-preventing signatures,” International Journal of Information Security, vol. 16, pp. 1–22, 2017. doi: 10.1007/s10207-015-0307-8 - DOI
MeSH terms
LinkOut - more resources
Full Text Sources