Energy-Efficient Anomaly Detection and Chaoticity in Electric Vehicle Driving Behavior
- PMID: 39275539
- PMCID: PMC11397768
- DOI: 10.3390/s24175628
Energy-Efficient Anomaly Detection and Chaoticity in Electric Vehicle Driving Behavior
Abstract
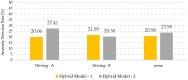
Detection of abnormal situations in mobile systems not only provides predictions about risky situations but also has the potential to increase energy efficiency. In this study, two real-world drives of a battery electric vehicle and unsupervised hybrid anomaly detection approaches were developed. The anomaly detection performances of hybrid models created with the combination of Long Short-Term Memory (LSTM)-Autoencoder, the Local Outlier Factor (LOF), and the Mahalanobis distance were evaluated with the silhouette score, Davies-Bouldin index, and Calinski-Harabasz index, and the potential energy recovery rates were also determined. Two driving datasets were evaluated in terms of chaotic aspects using the Lyapunov exponent, Kolmogorov-Sinai entropy, and fractal dimension metrics. The developed hybrid models are superior to the sub-methods in anomaly detection. Hybrid Model-2 had 2.92% more successful results in anomaly detection compared to Hybrid Model-1. In terms of potential energy saving, Hybrid Model-1 provided 31.26% superiority, while Hybrid Model-2 provided 31.48%. It was also observed that there is a close relationship between anomaly and chaoticity. In the literature where cyber security and visual sources dominate in anomaly detection, a strategy was developed that provides energy efficiency-based anomaly detection and chaotic analysis from data obtained without additional sensor data.
Keywords: Mahalanobis distance; anomaly detection; chaoticity; energy optimization; local outlier factor; long short-term memory; machine learning.
Conflict of interest statement
The authors declare no conflict of interest.
Figures









References
-
- Samariya D., Thakkar A. A Comprehensive Survey of Anomaly Detection Algorithms. Ann. Data Sci. 2023;10:829–850. doi: 10.1007/s40745-021-00362-9. - DOI
-
- Dalal S., Lilhore U.K., Foujdar N., Simaiya S., Ayadi M., Almujally N.A., Ksibi A. Next-Generation Cyber Attack Prediction for IoT Systems: Leveraging Multi-Class SVM and Optimized CHAID Decision Tree. J. Cloud Comput. 2023;12:137. doi: 10.1186/s13677-023-00517-4. - DOI
-
- Ghuge M., Ranjan N., Mahajan R.A., Upadhye P.A., Shirkande S.T., Bhamare D. Deep Learning Driven QoS Anomaly Detection for Network Performance Optimization. J. Electr. Syst. 2023;19:97–104. doi: 10.52783/jes.695. - DOI
-
- Jeffrey N., Tan Q., Villar J.R. A Hybrid Methodology for Anomaly Detection in Cyber–Physical Systems. Neurocomputing. 2024;568:127068. doi: 10.1016/j.neucom.2023.127068. - DOI
-
- Qin H., Yan M., Ji H. Application of Controller Area Network (CAN) Bus Anomaly Detection Based on Time Series Prediction. Veh. Commun. 2021;27:100291. doi: 10.1016/j.vehcom.2020.100291. - DOI
Grants and funding
LinkOut - more resources
Full Text Sources

