VAE-WACGAN: An Improved Data Augmentation Method Based on VAEGAN for Intrusion Detection
- PMID: 39338780
- PMCID: PMC11435708
- DOI: 10.3390/s24186035
VAE-WACGAN: An Improved Data Augmentation Method Based on VAEGAN for Intrusion Detection
Abstract
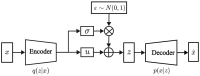
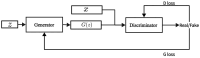
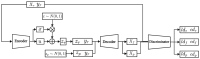
To address the class imbalance issue in network intrusion detection, which degrades performance of intrusion detection models, this paper proposes a novel generative model called VAE-WACGAN to generate minority class samples and balance the dataset. This model extends the Variational Autoencoder Generative Adversarial Network (VAEGAN) by integrating key features from the Auxiliary Classifier Generative Adversarial Network (ACGAN) and the Wasserstein Generative Adversarial Network with Gradient Penalty (WGAN-GP). These enhancements significantly improve both the quality of generated samples and the stability of the training process. By utilizing the VAE-WACGAN model to oversample anomalous data, more realistic synthetic anomalies that closely mirror the actual network traffic distribution can be generated. This approach effectively balances the network traffic dataset and enhances the overall performance of the intrusion detection model. Experimental validation was conducted using two widely utilized intrusion detection datasets, UNSW-NB15 and CIC-IDS2017. The results demonstrate that the VAE-WACGAN method effectively enhances the performance metrics of the intrusion detection model. Furthermore, the VAE-WACGAN-based intrusion detection approach surpasses several other advanced methods, underscoring its effectiveness in tackling network security challenges.
Keywords: dataset balancing; deep learning; generative adversarial network; network intrusion detection system (IDS); network security; variational autoencoder.
Conflict of interest statement
The authors declare no conflicts of interest.
Figures





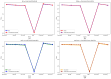
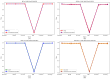
References
-
- Thakkar A., Lohiya R. A Review on Machine Learning and Deep Learning Perspectives of IDS for IoT: Recent Updates, Security Issues, and Challenges. Arch. Comput. Methods Eng. 2021;28:3211–3243. doi: 10.1007/s11831-020-09496-0. - DOI
-
- Papamartzivanos D., Gómez Mármol F., Kambourakis G. Dendron: Genetic trees driven rule induction for network intrusion detection systems. Future Gener. Comput. Syst. 2018;79:558–574. doi: 10.1016/j.future.2017.09.056. - DOI
-
- Hasan M.A.M., Nasser M., Pal B., Ahmad S. Support Vector Machine and Random Forest Modeling for Intrusion Detection System (IDS) J. Intell. Learn. Syst. Appl. 2014;06:45–52. doi: 10.4236/jilsa.2014.61005. - DOI
-
- Bedi P., Gupta N., Jindal V. I-SiamIDS: An improved Siam-IDS for handling class imbalance in network-based intrusion detection systems. Appl. Intell. 2021;51:1133–1151. doi: 10.1007/s10489-020-01886-y. - DOI
-
- Larsen A.B.L., Sønderby S.K., Larochelle H., Winther O. Autoencoding beyond pixels using a learned similarity metric; Proceedings of the 33rd International Conference on Machine Learning, Proceedings of Machine Learning Research; New York, NY, USA. 19–24 June 2016; pp. 1558–1566.
Grants and funding
LinkOut - more resources
Full Text Sources
Miscellaneous

