Generalised Entropy Accumulation
- PMID: 39403569
- PMCID: PMC11470903
- DOI: 10.1007/s00220-024-05121-4
Generalised Entropy Accumulation
Abstract
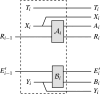
Consider a sequential process in which each step outputs a system and updates a side information register E. We prove that if this process satisfies a natural "non-signalling" condition between past outputs and future side information, the min-entropy of the outputs conditioned on the side information E at the end of the process can be bounded from below by a sum of von Neumann entropies associated with the individual steps. This is a generalisation of the entropy accumulation theorem (EAT) (Dupuis et al. in Commun Math Phys 379: 867-913, 2020), which deals with a more restrictive model of side information: there, past side information cannot be updated in subsequent rounds, and newly generated side information has to satisfy a Markov condition. Due to its more general model of side-information, our generalised EAT can be applied more easily and to a broader range of cryptographic protocols. As examples, we give the first multi-round security proof for blind randomness expansion and a simplified analysis of the E91 QKD protocol. The proof of our generalised EAT relies on a new variant of Uhlmann's theorem and new chain rules for the Rényi divergence and entropy, which might be of independent interest.
© The Author(s) 2024.
Conflict of interest statement
Conflict of interestThe authors have no Conflict of interest to declare.
Figures

References
-
- Renner, R.: Security of quantum key distribution. Int. J. Quantum Inf. 6(01), 1–127 (2008) - DOI
-
- Tomamichel, M., Colbeck, R., Renner, R.: A fully quantum asymptotic equipartition property. IEEE Trans. Inf. Theory 55(12), 5840–5847 (2009) - DOI
-
- Bamps, C., Massar, S., Pironio, S.: Device-independent randomness generation with sublinear shared quantum resources. Quantum 2, 86 (2018) - DOI
LinkOut - more resources
Full Text Sources
Research Materials
Miscellaneous
