The Design and Implementation of Kerberos-Blockchain Vehicular Ad-Hoc Networks Authentication Across Diverse Network Scenarios
- PMID: 39685965
- PMCID: PMC11644313
- DOI: 10.3390/s24237428
The Design and Implementation of Kerberos-Blockchain Vehicular Ad-Hoc Networks Authentication Across Diverse Network Scenarios
Abstract
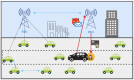
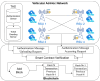
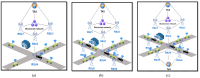
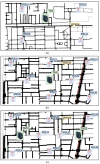
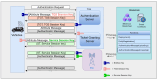
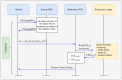
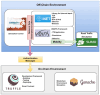
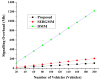
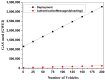
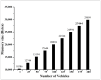
Vehicular Ad-Hoc Networks (VANETs) play an essential role in the intelligent transportation era, furnishing users with essential roadway data to facilitate optimal route selection and mitigate the risk of accidents. However, the network exposure makes VANETs susceptible to cyber threats, making authentication crucial for ensuring security and integrity. Therefore, joining entity verification is essential to ensure the integrity and security of communication in VANETs. However, to authenticate the entities, authentication time should be minimized to guarantee fast and secure authentication procedures. We propose an authentication system for VANETs using blockchain and Kerberos for storing authentication messages in a blockchain ledger accessible to Trusted Authentication Servers (TASs) and Roadside Units (RSUs). We evaluate the system in three diverse network scenarios: suburban, urban with 1 TAS, and urban with 2 TASs. The findings reveal that this proposal is applicable in diverse network scenarios to fulfill the network requirements, including authentication, handover, and end-to-end delay, considering an additional TAS for an increasing number of vehicles. The system is also practicable in storing the authentication message in blockchain considering the gas values and memory size for all scenarios.
Keywords: Kerberos authentication; Vehicular Ad-Hoc Network; blockchain.
Conflict of interest statement
The authors declare no conflicts of interest.
Figures


References
-
- Rashid S.A., Audah L., Hamdi M.M. Intelligent Transportation Systems (ITSs) in VANET and MANET. In: Dehuri S., Prasad Mishra B.S., Mallick P.K., Cho S.B., editors. Biologically Inspired Techniques in Many Criteria Decision Making. Smart Innovation, Systems and Technologies. Volume 271. Springer; Singapore: 2022. pp. 6–59.
-
- Ali R., Liu R., Nayyar A., Waris I., Li L., Shah M.A. Intelligent Driver Model-Based Vehicular Ad Hoc Network Communication in Real-Time Using 5G New Radio Wireless Networks. IEEE Access. 2023;11:4956–4971. doi: 10.1109/ACCESS.2023.3234964. - DOI
-
- Bhanu C. Cloud and IoT-Based Vehicular Ad Hoc Networks. Wiley; Hoboken, NJ, USA: 2021. Challenges, Benefits and Issues: Future Emerging VANETs and Cloud Approaches; pp. 142–149.
-
- Qu F., Wu Z., Wang F., Cho W. A Security and Privacy Review of VANETs. IEEE Trans. Intell. Transp. Syst. 2016;16:2985–2996. doi: 10.1109/TITS.2015.2439292. - DOI
-
- Jan S.A., Amin N.U., Othman M., Ali M., Umar A.I., Basir A. A Survey on Privacy-Preserving Authentication Schemes in VANETs: Attacks, Challenges and Open Issues. IEEE Access. 2021;9:153701–153726. doi: 10.1109/ACCESS.2021.3125521. - DOI
LinkOut - more resources
Full Text Sources

