A cost-effective adaptive repair strategy to mitigate DDoS-capable IoT botnets
- PMID: 39724180
- PMCID: PMC11670966
- DOI: 10.1371/journal.pone.0301888
A cost-effective adaptive repair strategy to mitigate DDoS-capable IoT botnets
Abstract
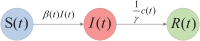
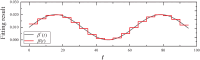
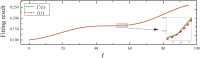
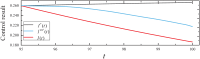
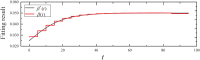
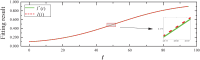
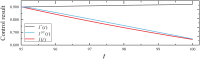
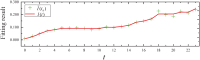
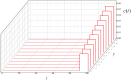
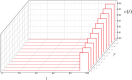
Distributed denial of service (DDoS) is a type of cyberattack in which multiple compromised systems flood the bandwidth or resources of a single system, making the flooded system inaccessible to legitimate users. Since large-scale botnets based on the Internet of Things (IoT) have been hotbeds for launching DDoS attacks, it is crucial to defend against DDoS-capable IoT botnets effectively. In consideration of resource constraints and frequent state changes for IoT devices, they should be equipped with repair measures that are cost-effective and adaptive to mitigate the impact of DDoS attacks. From the mitigation perspective, we refer to the collection of repair costs at all times as a repair strategy. This paper is then devoted to studying the problem of developing a cost-effective and adaptive repair strategy (ARS). First, we establish an IoT botware propagation model that fully captures the state evolution of an IoT network under attack and defense interventions. On this basis, we model the ARS problem as a data-driven optimal control problem, aiming to realize both learning and prediction of propagation parameters based on network traffic data observed at multiple discrete time slots and control of IoT botware propagation to a desired infection level. By leveraging optimal control theory, we propose an iterative algorithm to solve the problem, numerically obtaining the learned time-varying parameters and a repair strategy. Finally, the performance of the learned parameters and the resulting strategy are examined through computer experiments.
Copyright: © 2024 Hu, Yang. This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Conflict of interest statement
The authors have declared that no competing interests exist.
Figures
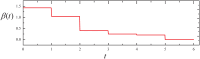
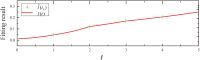
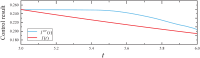
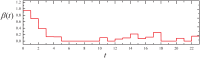
Similar articles
-
Blockchain Based Solutions to Mitigate Distributed Denial of Service (DDoS) Attacks in the Internet of Things (IoT): A Survey.Sensors (Basel). 2022 Jan 31;22(3):1094. doi: 10.3390/s22031094. Sensors (Basel). 2022. PMID: 35161838 Free PMC article. Review.
-
Adaptive Machine Learning Based Distributed Denial-of-Services Attacks Detection and Mitigation System for SDN-Enabled IoT.Sensors (Basel). 2022 Mar 31;22(7):2697. doi: 10.3390/s22072697. Sensors (Basel). 2022. PMID: 35408312 Free PMC article.
-
DDoS Attack Prevention for Internet of Thing Devices Using Ethereum Blockchain Technology.Sensors (Basel). 2022 Sep 8;22(18):6806. doi: 10.3390/s22186806. Sensors (Basel). 2022. PMID: 36146163 Free PMC article.
-
Software-Defined-Networking-Based One-versus-Rest Strategy for Detecting and Mitigating Distributed Denial-of-Service Attacks in Smart Home Internet of Things Devices.Sensors (Basel). 2024 Aug 3;24(15):5022. doi: 10.3390/s24155022. Sensors (Basel). 2024. PMID: 39124069 Free PMC article.
-
Systematic Literature Review of IoT Botnet DDOS Attacks and Evaluation of Detection Techniques.Sensors (Basel). 2024 Jun 1;24(11):3571. doi: 10.3390/s24113571. Sensors (Basel). 2024. PMID: 38894365 Free PMC article. Review.
References
-
- Greengard S. The internet of things, MIT press, 2021.
-
- Etemadi M, Ghobaei-Arani M, Shahidinejad A. A cost-efficient auto-scaling mechanism for IoT applications in fog computing environment: a deep learning-based approach. Cluster Computing. 2021;24(4):3277–92. doi: 10.1007/s10586-021-03307-2 - DOI
-
- Reiss-Mirzaei M, Ghobaei-Arani M, Esmaeili L. A review on the edge caching mechanisms in the mobile edge computing: A social-aware perspective. Internet of Things. 2023:100690. doi: 10.1016/j.iot.2023.100690 - DOI
-
- Khanday SA, Fatima H, Rakesh N. Implementation of intrusion detection model for DDoS attacks in lightweight IoT networks. Expert Systems with Applications. 2023;215:119330. doi: 10.1016/j.eswa.2022.119330 - DOI
-
- Kumari P, Jain AK. A comprehensive study of DDoS attacks over IoT network and their countermeasures. Computers & Security. 2023:103096. doi: 10.1016/j.cose.2023.103096 - DOI
MeSH terms
LinkOut - more resources
Full Text Sources

