Embedding Trust in the Media Access Control Protocol for Wireless Networks
- PMID: 39860724
- PMCID: PMC11769031
- DOI: 10.3390/s25020354
Embedding Trust in the Media Access Control Protocol for Wireless Networks
Abstract
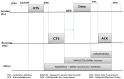
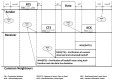
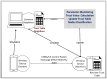
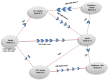
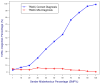
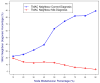
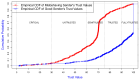
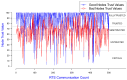
IEEE 802.11 is one of the most common medium access control (MAC) protocols used in wireless networks. The carrier sense multiple access with collision avoidance (CSMA/CA) mechanisms in 802.11 have been designed under the assumption that all nodes in the network are cooperative and trustworthy. However, the potential for non-cooperative nodes exists, nodes that may purposefully misbehave in order to, for example, obtain extra bandwidth, conserve their resources, or disrupt network performance. This issue is further compounded when receivers such as Wi-Fi hotspots, normally trusted by other module nodes, also misbehave. Such issues, their detection, and mitigation have, we believe, not been sufficiently addressed in the literature. This research proposes a novel trust-incorporated MAC protocol (TMAC) which detects and mitigates complex node misbehavior for distributed network environments. TMAC introduces three main features into the original IEEE 802.11 protocol. First, each node assesses a trust level for their neighbors, establishing a verifiable backoff value generation mechanism with an incorporated trust model involving senders, receivers, and common neighbors. Second, TMAC uses a collaborative penalty scheme to penalize nodes that deviate from the IEEE 802.11 protocol. This feature removes the assumption of a trusted receiver. Third, a TMAC diagnosis mechanism is carried out for each distributed node periodically, to reassess neighbor status and to reclassify each based on their trust value. Simulation results in ns2 showed that TMAC is effective in diagnosing and starving selfish or misbehaving nodes in distributed wireless networks, improving the performance of trustworthy well-behaving nodes. The significant feature of TMAC is its ability to detect sender, receiver, and colluding node misbehavior at the MAC layer with a high level of accuracy, without the need to trust any of the communicating parties.
Keywords: CSMA/CA; IEEE 802.11; MAC; network security; trust; wireless networks.
Conflict of interest statement
The authors declare no conflicts of interest.
Figures


References
-
- IEEE Standard for Information Technology—Specific Requirements Part 11: Wireless LAN Medium Access Control (IEEE) and Physical Layer (IEEE) Specifications. IEEE; Piscataway, NJ, USA: 2012. pp. 1–5229.
-
- Pham C. Investigating and experimenting CSMA channel access mechanisms for LoRa IoT networks; Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC); Barcelona, Spain. 15–18 April 2018; pp. 1–6. - DOI
-
- Sangeetha U., Babu A.V. Performance analysis of IEEE 802.11ah wireless local area network under the restricted access window-based mechanism. Int. J. Commun. Syst. 2019;32:e3888. doi: 10.1002/dac.3888. - DOI
-
- Alocious C., Xiao H., Christianson B. Analysis of DoS attacks at MAC Layer in mobile adhoc networks; Proceedings of the 2015 International Wireless Communications and Mobile Computing Conference (IWCMC); Dubrovnik, Croatia. 24–28 August 2015; pp. 811–816. - DOI
-
- Alocious C., Xiao H., Christianson B., Malcolm J. Evaluation and Prevention of MAC Layer Misbehaviours in Public Wireless Hotspots; Proceedings of the IEEE International Conference on Dependable, Autonomic and Secure Computing. DASC’13; Liverpool, UK. 26–28 October 2015; Piscataway, NJ, USA: IEEE; 2015.
LinkOut - more resources
Full Text Sources

