Integrity verified lightweight ciphering for secure medical image sharing between embedded SoCs
- PMID: 40032946
- PMCID: PMC11876590
- DOI: 10.1038/s41598-025-91431-z
Integrity verified lightweight ciphering for secure medical image sharing between embedded SoCs
Abstract
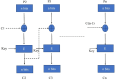
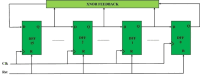
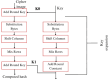
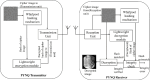
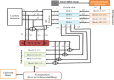
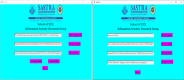
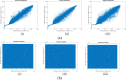
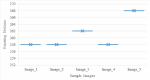
In the age of digital communication, safeguarding the security and integrity of transmitted images is crucial, especially for online and real-time applications where data privacy is paramount. This paper addresses the problem of protecting sensitive medical images during transmission by proposing a robust, lightweight encryption scheme. The proposed method uses keys derived from the Lorentz attractor for diffusion and a 16-bit Linear Feedback Shift Register (LFSR) for pseudo-random confusion. Additionally, the Cipher Block Chaining (CBC) process enhances the encryption output to ensure stronger security. A 512-bit hashing scheme using the Whirlpool algorithm is implemented to maintain data integrity, providing a robust hash comparison mechanism. The obtained hash values achieve a Hamming distance of 46.5-53.3% against the ideal value of 50%, demonstrating its high sensitivity. Furthermore, a custom-tailored lightweight symmetric key encryption secures the hash values before transmission from the sender alongside the encrypted images. At the receiver end, the hash is decrypted and compared with the extracted hash from the received cipher image to verify integrity, enabling secure decryption. The encrypted DICOM images achieve an average entropy value of 7.99752, a PSNR of 5.872 dB, NPCR of 99.66128%, and a UACI of 33.55964%, while the noise attack analysis further demonstrates its robustness. The entire process was implemented and tested on Xilinx PYNQ-Z1 System on Chip (SoC) boards, with user interaction facilitated through a custom-designed Graphical User Interface (GUI). The experimental results confirm the scheme's effectiveness in securing medical images while maintaining integrity and resilience against attacks, making it suitable for real-time and wireless applications.
Keywords: Data attack; Encryption; FPGA; Hash function; Lightweight; SoC.
© 2025. The Author(s).
Conflict of interest statement
Declarations. Competing interests: The authors declare no competing interests. Ethics approval: All authors have read, understood, and have complied as applicable with the statement on “Ethical responsibilities of Authors” as found in the Instructions for Authors.
Figures









References
-
- Shannon, C. E. Communication theory of secrecy systems. Bell Syst. Tech. J.28(4), 656–715. 10.1002/j.1538-7305.1949.tb00928.x (1949).
-
- Jawed, M. S. & Sajid, M. COBLAH: A chaotic OBL initialized hybrid Algebraic-Heuristic algorithm for optimal S-Box construction. Comput. Stand. Interfaces10389010.1016/j.csi.2024.103890 (2024).
-
- Dash, A. & Naik, K. Protection of medical images through MFDCuT and SA-BSO. Multimed. Tools Appl., 1–52. 10.1007/s11042-024-19230-8 (2024).
-
- Sayah, M. M., Redouane, K. M. & Amine, K. Secure transmission and integrity verification for color medical images in telemedicine applications. Multimed Tools Appl.81, 43613–43638. 10.1007/s11042-021-11791-2 (2022).
-
- Mohamed, H. I., Alhammad, S. M., Khafaga, D. S., Komy, O. E. & Hosny, K. M. A new image encryption scheme based on the hybridization of Lorenz chaotic map and fibonacci Q-Matrix. IEEE Access.12, 14764–14775. 10.1109/ACCESS.2023.3341103 (2024).
Grants and funding
LinkOut - more resources
Full Text Sources
Miscellaneous

