AI-driven cybersecurity framework for software development based on the ANN-ISM paradigm
- PMID: 40251237
- PMCID: PMC12008409
- DOI: 10.1038/s41598-025-97204-y
AI-driven cybersecurity framework for software development based on the ANN-ISM paradigm
Abstract
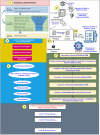
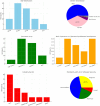
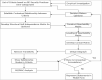
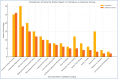
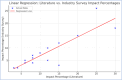
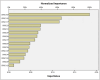
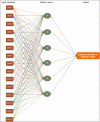
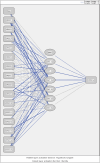
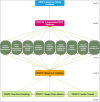
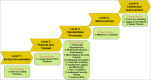
With the increasing reliance on software applications, cybersecurity threats have become a critical concern for developers and organizations. The answer to this vulnerability is AI systems, which help us adapt a little better, as traditional measures in security have failed to respond to the upcoming threats. This paper presents an innovative cybersecurity framework using AI, by the Artificial Neural Network (ANN)-Interpretive Structural Modeling (ISM) model, to improve threat detection, vulnerability assessment, and risk response during software development. This framework helps realize dynamic, intelligent security as a part of the Software Development life cycle (SDLC). Initially, existing cybersecurity risks in software coding are systematically evaluated to identify potential gaps and integrate best practices into the proposed model. In the second phase, an empirical survey was conducted to identify and validate the findings of the systematic literature review (SLR). In the third phase, a hybrid approach is employed, integrating ANN for real-time threat detection and risk assessment. It utilizes ISM to analyze the relationships between cybersecurity risks and vulnerabilities, creating a structured framework for understanding interdependencies. A case study was conducted in the last stage to test and evaluate the AI-driven cybersecurity Mitigation Model for Secure Software Coding. A multi-level categorization system is also used to assess maturity across five key levels: Ad hoc, Planned, Standardized, Metrics-Driven, and Continuous Improvements. This study identifies 15 cybersecurity risks and vulnerabilities in software coding, along with 158 AI-driven best practices for mitigating these risks. It also identifies critical areas of insecure coding practices and develops a scalable model to address cybersecurity risks across different maturity levels. The results show that AI outperforms traditional systems in detecting security weaknesses and simultaneously fixing problems. During Levels 1-3 of the system improvement process, advanced security methods are used to protect against threats. Our analysis reveals that organizations at Levels 4 and 5 still need to entirely shift to using AI-based protection tools and techniques. The proposed system provides developers and managers with valuable insights, enabling them to select security enhancements tailored to their organization's development stages. It supports automated threat analysis, helping organizations stay vigilant against potential cybersecurity threats. The study introduces a novel ANN-ISM framework integrating AI tools with cybersecurity modeling formalisms. By merging AI systems with secure software coding principles, this research enhances the connection between AI-generated insights and real-world cybersecurity usage.
Keywords: AI; ANN-ISM modeling; Case study; Cybersecurity maturity levels; Cybersecurity risks and practices; Empirical survey; Secure software coding; Systematic literature review.
© 2025. The Author(s).
Conflict of interest statement
Declarations. Competing interests: The authors declare no competing interests.
Figures
References
-
- Chanda, R. C., Vafaei-Zadeh, A., Hanifah, H. & Nikbin, D. Assessing cybersecurity awareness among bank employees: A multi-stage analytical approach using PLS-SEM, ANN, and fsQCA in a developing country context. Comput. Secur.149, 104208 (2025). - DOI
-
- Alsirhani, A. et al. Implementation of African vulture optimization algorithm based on deep learning for cybersecurity intrusion detection. Alex. Eng. J.79, 105–115 (2023). - DOI
-
- Alzahrani, A. & Khan, R. A. Secure software design evaluation and decision making model for ubiquitous computing: A two-stage ANN-Fuzzy AHP approach. Comput. Hum. Behav.153, 108109 (2023). - DOI
-
- Ding, A., Li, G., Yi, X., Lin, X., Li, J. & Zhang, C. Generative artificial intelligence for software security analysis: Fundamentals, applications, and challenges. IEEE Softw.41(6), 1–8 (2024).
-
- Al-Mhiqani, M. N. et al. Insider threat detection in cyber-physical systems: A systematic literature review. Comput. Electr.l Eng.119, 109489 (2024). - DOI
MeSH terms
LinkOut - more resources
Full Text Sources

