Revisiting Wireless Cyberattacks on Vehicles
- PMID: 40285290
- PMCID: PMC12031412
- DOI: 10.3390/s25082605
Revisiting Wireless Cyberattacks on Vehicles
Abstract
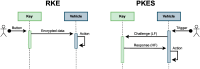
The automotive industry has been a prime target for cybercriminals for decades, with attacks becoming more sophisticated as vehicles integrate advanced digital technologies. In response, new standards and regulations have been introduced, requiring manufacturers to implement robust cybersecurity measures to obtain necessary certifications. Modern vehicles have an extensive attack surface due to the increasing number of interconnected electronic components and wireless communication features. While new technologies improve connectivity, automation, and comfort, they also introduce new vulnerabilities that can be exploited by attackers. This paper presents a comprehensive analysis of the attack surface of modern vehicles, focusing on the security risks associated with wireless communication technologies. Each technology is examined in detail, highlighting existing research, known vulnerabilities, and potential countermeasures. Furthermore, this study identifies key research gaps in the field, providing insights into critical areas that require further investigation. This work aims to guide future research efforts in order to enhance vehicle cybersecurity in the evolving landscape of smart, autonomous, and connected vehicles.
Keywords: cyberattacks; radio frequency; vehicles; wireless.
Conflict of interest statement
The authors declare no conflicts of interest.
Figures
References
-
- UNECE . UN Regulation No. 155—Cyber Security and Cyber Security Management System. UNECE; Geneva, Switzerland: 2021.
-
- UNECE . UN Regulation No. 156—Software Update and Software Update Management System. UNECE; Geneva, Switzerland: 2021.
-
- Girdhar M., Hong J., Moore J. Cybersecurity of Autonomous Vehicles: A Systematic Literature Review of Adversarial Attacks and Defense Models. IEEE Open J. Veh. Technol. 2023;4:417–437. doi: 10.1109/OJVT.2023.3265363. - DOI
-
- Car Hacking Village. [(accessed on 22 January 2025)]. Available online: https://www.carhackingvillage.com.
-
- Enabling Positive Security Solutions for the Automotive Market. [(accessed on 22 January 2025)]. Available online: https://asrg.io.
Publication types
LinkOut - more resources
Full Text Sources