A Decentralized Signcryption Scheme Based on CFL
- PMID: 40292854
- PMCID: PMC11945482
- DOI: 10.3390/s25061773
A Decentralized Signcryption Scheme Based on CFL
Abstract
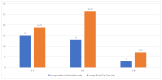
The rapid advancement of quantum computing technology poses a significant threat to conventional public key cryptographic infrastructure. The SM2 (state key cryptography algorithm no. 2) elliptic curve public key cryptographic algorithm, which adopts elliptic curve cryptography, has demonstrated strong resistance to quantum attacks. However, existing signcryption schemes remain vulnerable due to their reliance on a single certification authority (CA) managing all keys. The cryptography fundamental logics (CFL) authentication process eliminates the need for third-party involvement, achieving decentralized authentication and reducing the burden on certificate generation centers. Therefore, a decentralized signcryption scheme based on CFL was proposed using the SM2 national cryptographic algorithm. Unlike traditional signcryption schemes, this approach does not depend on the certification authority's private key during the public-private key generation process. This innovation helps avoid risks associated with certification authority private key leakage and ensures decentralized characteristics. The proposed scheme was rigorously verified under the random oracle model (ROM) and based on the complexity assumption of the elliptic curve Diffie-Hellman (ECDH) problem. The theoretical analysis and experimental results demonstrate that compared to traditional methods, the proposed scheme exhibits higher efficiency in communication and computation. Specifically, the proposed scheme reduces computational overheads by approximately 30% and communication overheads by approximately 20% in practical working environments. These quantitative improvements highlight the scheme's promising application prospects and practical value.
Keywords: CFL; SM2; provable security; random oracle model; signcryption.
Conflict of interest statement
Author Leyi Shi was employed by the company Qingdao Guochuang Intelligent Appliance Research Institute Co., Ltd. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Figures
Similar articles
-
An efficient certificateless anonymous signcryption communication scheme for vehicular adhoc network.Sci Rep. 2024 Nov 7;14(1):27079. doi: 10.1038/s41598-024-77992-5. Sci Rep. 2024. PMID: 39511283 Free PMC article.
-
Efficient certificate-based signcryption secure against public key replacement attacks and insider attacks.ScientificWorldJournal. 2014;2014:295419. doi: 10.1155/2014/295419. Epub 2014 May 12. ScientificWorldJournal. 2014. PMID: 24959606 Free PMC article.
-
A Conditional Privacy Preserving Generalized Ring Signcryption Scheme for Micro Aerial Vehicles.Micromachines (Basel). 2022 Nov 8;13(11):1926. doi: 10.3390/mi13111926. Micromachines (Basel). 2022. PMID: 36363947 Free PMC article.
-
A heterogeneous signcryption scheme for smart grid with trusted multi-ciphertext equality test.Math Biosci Eng. 2023 Nov 8;20(11):20295-20316. doi: 10.3934/mbe.2023898. Math Biosci Eng. 2023. PMID: 38052646
-
Quantum attack-resistent certificateless multi-receiver signcryption scheme.PLoS One. 2013 Jun 5;8(6):e49141. doi: 10.1371/journal.pone.0049141. eCollection 2013. PLoS One. 2013. PMID: 23967037 Free PMC article.
References
-
- Zheng Y. Digital Signcryption or How to Achieve Cost(Signature & Encryption) << Cost(Signature) + Cost(Encryption); Proceedings of the Annual International Cryptology Conference; Santa Barbara, CA, USA. 17–21 August 1997.
-
- Yu H.F., Qiao Y.F., Meng R. Quantum-resistant attribute-based threshold ring signcryption scheme for blockchain finance. Inf. Netw. Secur. 2023;23:44–52.
-
- Ke-Zhen Z., Jing-Qiang L., Wei W., Yong L., Guang-Zheng L., Zhen-Ya L. Research on Two-Party SM2 Threshold Signature Schemes with a Blind Cooperative Server. J. Cryptologic Res. 2024;11:945–962. doi: 10.13868/j.cnki.jcr.000718. - DOI
-
- Wang X., Qian H. Attacks against Two Identity-Based Signcryption Schemes; Proceedings of the Second International Conference on Networks Security, Wireless Communications and Trusted Computing; Wuhan, China. 24–25 April 2010.
-
- Xie Z., Chen Y., Ali I., Pan C., Li F., He W. Efficient and Secure Certificateless Signcryption Without Pairing for Edge Computing-Based Internet of Vehicles. IEEE Trans. Veh. Technol. 2023;72:5642–5653. doi: 10.1109/TVT.2022.3230442. - DOI
LinkOut - more resources
Full Text Sources