Mathematical analysis of the dynamics of cyberattack propagation in IoT networks
- PMID: 40378094
- PMCID: PMC12083842
- DOI: 10.1371/journal.pone.0322391
Mathematical analysis of the dynamics of cyberattack propagation in IoT networks
Abstract
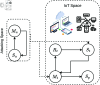
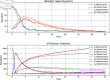
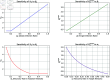
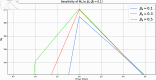
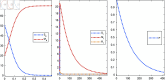
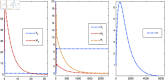
The growing threat of cyberattacks is a severe concern to governments, military organizations, and industries, especially with the increasing use of Internet of Things (IoT) devices. To tackle this issue, researchers are working on ways to predict and prevent these attacks by studying how malware spreads. In this study, we use a discrete-time approach to better model how cyberattacks spread across IoT networks. We also focus on the role of firewalls, developing a strategy to optimize their effectiveness in slowing down the spread of malware. Additionally, we analyze the reproduction number's sensitivity and explore the proposed discrete system's local and global stability. The model was simulated and analyzed using Python packages, providing practical solutions to improve cybersecurity in IoT networks. These insights are supported by numerical simulations based on real-world data.
Copyright: © 2025 AbuHour et al. This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Conflict of interest statement
The authors have declared that no competing interests exist.
Figures
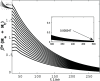
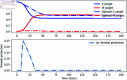
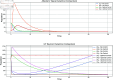
Similar articles
-
A Malware Distribution Simulator for the Verification of Network Threat Prevention Tools.Sensors (Basel). 2021 Oct 21;21(21):6983. doi: 10.3390/s21216983. Sensors (Basel). 2021. PMID: 34770290 Free PMC article.
-
A cost-effective adaptive repair strategy to mitigate DDoS-capable IoT botnets.PLoS One. 2024 Dec 26;19(12):e0301888. doi: 10.1371/journal.pone.0301888. eCollection 2024. PLoS One. 2024. PMID: 39724180 Free PMC article.
-
Malware Detection in Internet of Things (IoT) Devices Using Deep Learning.Sensors (Basel). 2022 Nov 29;22(23):9305. doi: 10.3390/s22239305. Sensors (Basel). 2022. PMID: 36502007 Free PMC article.
-
A Comprehensive Study of Anomaly Detection Schemes in IoT Networks Using Machine Learning Algorithms.Sensors (Basel). 2021 Dec 13;21(24):8320. doi: 10.3390/s21248320. Sensors (Basel). 2021. PMID: 34960414 Free PMC article. Review.
-
The elephant in the room: cybersecurity in healthcare.J Clin Monit Comput. 2023 Oct;37(5):1123-1132. doi: 10.1007/s10877-023-01013-5. Epub 2023 Apr 24. J Clin Monit Comput. 2023. PMID: 37088852 Free PMC article. Review.
References
-
- Alashhab ZR, Anbar M, Singh MM, Hasbullah IH, Jain P, Al-Amiedy TA. Distributed Denial of service attacks against cloud computing environment: survey, issues, challenges and coherent taxonomy. Appl Sci 2022;12(23):12441. 10.3390/app122312441 - DOI
-
- Ahmad A, Abu-Hour Y, DarAssi MH. Effects of computer networks’ viruses under the of removable devices. Int J Dyn Syst Differ Equ 2020;10(3):233–48. doi: 10.1504/IJDSDE.2020.107808 - DOI
-
- De Neira AB, Kantarci B, Nogueira M. Distributed denial of service attack prediction: challenges, open issues and opportunities. Comput Netw. 2023;222:109553. doi: 10.1016/j.comnet.2022.109553 - DOI
-
- Kumar V, Kumar V, Sinha D, Das AK. Simulation analysis of DDoS attack in IoT environment. In: 4th International Conference on Internet of Things and Connected Technologies (ICIoTCT), 2019: Internet of Things and Connected Technologies. Springer; 2020. pp. 77–87.
-
- Machaka P, Ajayi O, Kahenga F, Bagula A, Kyamakya K. Modelling DDoS attacks in IoT networks using machine learning. In: International Conference on Emerging Technologies for Developing Countries. Springer; 2022. pp. 161–75.
MeSH terms
LinkOut - more resources
Full Text Sources

