Beacon Reconstruction Attack: Reconstruction of genomes in genomic data-sharing beacons using summary statistics
- PMID: 40388204
- PMCID: PMC12133290
- DOI: 10.1093/bioinformatics/btaf273
Beacon Reconstruction Attack: Reconstruction of genomes in genomic data-sharing beacons using summary statistics
Abstract
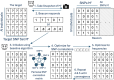
Motivation: Genomic data-sharing beacon protocol, developed by the Global Alliance for Genomics and Health, offers a privacy-preserving mechanism for querying genomic datasets while restricting direct data access. Despite their design, beacons remain vulnerable to privacy attacks. This study introduces a novel privacy vulnerability of the protocol: one can reconstruct large portions of the genomes of all beacon participants by only using the summary statistics reported by the protocol.
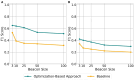
Results: We introduce a novel optimization-based algorithm that leverages beacon responses and SNP correlations for reconstruction. By optimizing for the SNP correlations and allele frequencies, the proposed approach achieves genome reconstruction with a substantially higher F1-score (70%) compared to baseline methods (45%) on beacons generated using individuals from the HapMap and OpenSNP datasets. We show that reconstructed genomes can be used by downstream applications such as in membership inference attacks against other beacons. Our findings reveal that beacons releasing allele frequencies substantially increase the reconstruction risk, underscoring the need for enhanced privacy-preserving mechanisms to protect genomic data.
Availability and implementation: Our implementation is available at https://github.com/ASAP-Bilkent/Beacon-Reconstruction-Attack.
© The Author(s) 2025. Published by Oxford University Press.
Figures
Similar articles
-
Signs and symptoms to determine if a patient presenting in primary care or hospital outpatient settings has COVID-19.Cochrane Database Syst Rev. 2022 May 20;5(5):CD013665. doi: 10.1002/14651858.CD013665.pub3. Cochrane Database Syst Rev. 2022. PMID: 35593186 Free PMC article.
-
A New Measure of Quantified Social Health Is Associated With Levels of Discomfort, Capability, and Mental and General Health Among Patients Seeking Musculoskeletal Specialty Care.Clin Orthop Relat Res. 2025 Apr 1;483(4):647-663. doi: 10.1097/CORR.0000000000003394. Epub 2025 Feb 5. Clin Orthop Relat Res. 2025. PMID: 39915110
-
Does Augmenting Irradiated Autografts With Free Vascularized Fibula Graft in Patients With Bone Loss From a Malignant Tumor Achieve Union, Function, and Complication Rate Comparably to Patients Without Bone Loss and Augmentation When Reconstructing Intercalary Resections in the Lower Extremity?Clin Orthop Relat Res. 2025 Jun 26. doi: 10.1097/CORR.0000000000003599. Online ahead of print. Clin Orthop Relat Res. 2025. PMID: 40569278
-
Home telemonitoring and remote feedback between clinic visits for asthma.Cochrane Database Syst Rev. 2016 Aug 3;2016(8):CD011714. doi: 10.1002/14651858.CD011714.pub2. Cochrane Database Syst Rev. 2016. PMID: 27486836 Free PMC article.
-
Can a Liquid Biopsy Detect Circulating Tumor DNA With Low-passage Whole-genome Sequencing in Patients With a Sarcoma? A Pilot Evaluation.Clin Orthop Relat Res. 2025 Jan 1;483(1):39-48. doi: 10.1097/CORR.0000000000003161. Epub 2024 Jun 21. Clin Orthop Relat Res. 2025. PMID: 38905450
References
-
- Cho H, Simmons S, Kim R et al. Privacy-preserving biomedical database queries with optimal privacy-utility trade-offs. Cell Syst 2020;10:408–16.e9. - PubMed
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources

