A novel dilated weighted recurrent neural network (RNN)-based smart contract for secure sharing of big data in Ethereum blockchain using hybrid encryption schemes
- PMID: 40567711
- PMCID: PMC12193487
- DOI: 10.7717/peerj-cs.2930
A novel dilated weighted recurrent neural network (RNN)-based smart contract for secure sharing of big data in Ethereum blockchain using hybrid encryption schemes
Abstract
Background: With the enhanced data amount being created, it is significant to various organizations and their processing, and managing big data becomes a significant challenge for the managers of the data. The development of inexpensive and new computing systems and cloud computing sectors gave qualified industries to gather and retrieve the data very precisely however securely delivering data across the network with fewer overheads is a demanding work. In the decentralized framework, the big data sharing puts a burden on the internal nodes among the receiver and sender and also creates the congestion in network. The internal nodes that exist to redirect information may have inadequate buffer ability to momentarily take the information and again deliver it to the upcoming nodes that may create the occasional fault in the transmission of data and defeat frequently. Hence, the next node selection to deliver the data is tiresome work, thereby resulting in an enhancement in the total receiving period to allocate the information.
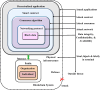
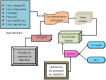
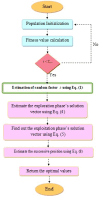
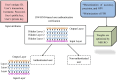
Methods: Blockchain is the primary distributed device with its own approach to trust. It constructs a reliable framework for decentralized control via multi-node data repetition. Blockchain is involved in offering a transparency to the application of transmission. A simultaneous multi-threading framework confirms quick data channeling to various network receivers in a very short time. Therefore, an advanced method to securely store and transfer the big data in a timely manner is developed in this work. A deep learning-based smart contract is initially designed. The dilated weighted recurrent neural network (DW-RNN) is used to design the smart contract for the Ethereum blockchain. With the aid of the DW-RNN model, the authentication of the user is verified before accessing the data in the Ethereum blockchain. If the authentication of the user is verified, then the smart contracts are assigned to the authorized user. The model uses elliptic Curve ElGamal cryptography (EC-EC), which is a combination of elliptic curve cryptography (ECC) and ElGamal encryption for better security, to make sure that big data transfers on the Ethereum blockchain are safe. The modified Al-Biruni earth radius search optimization (MBERSO) algorithm is used to make the best keys for this EC-EC encryption scheme. This algorithm manages keys efficiently and securely, which improves data security during blockchain operations.
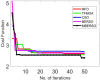
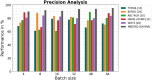
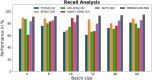
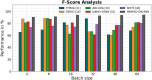
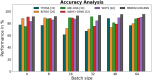
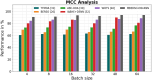
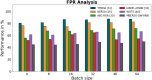
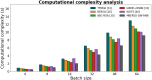
Results: The processes of encryption facilitate the secure transmission of big data over the Ethereum blockchain. Experimental analysis is carried out to prove the efficacy and security offered by the suggested model in transferring big data over blockchain via smart contracts.
Keywords: Big data sharing; Blockchain; Dilated weighted Recurrent neural network; Elliptic Curve-Elgamal cryptography; Key optimization; Modified Al-Biruni earth radius search optimization; Smart contract.
© 2025 S and P M.
Conflict of interest statement
The authors declare that they have no competing interests.
Figures
Similar articles
-
Automatic Recommender System of Development Platforms for Smart Contract-Based Health Care Insurance Fraud Detection Solutions: Taxonomy and Performance Evaluation.J Med Internet Res. 2024 Oct 18;26:e50730. doi: 10.2196/50730. J Med Internet Res. 2024. PMID: 39423005 Free PMC article.
-
Blockchain Integration With Digital Technology and the Future of Health Care Ecosystems: Systematic Review.J Med Internet Res. 2021 Nov 2;23(11):e19846. doi: 10.2196/19846. J Med Internet Res. 2021. PMID: 34726603 Free PMC article.
-
Designing A Blockchain-Empowered Telehealth Artifact for Decentralized Identity Management and Trustworthy Communication: Interdisciplinary Approach.J Med Internet Res. 2024 Sep 25;26:e46556. doi: 10.2196/46556. J Med Internet Res. 2024. PMID: 39320943 Free PMC article.
-
Design of an improved graph-based model integrating LSTM, LoRaWAN, and blockchain for smart agriculture.PeerJ Comput Sci. 2025 Jun 20;11:e2896. doi: 10.7717/peerj-cs.2896. eCollection 2025. PeerJ Comput Sci. 2025. PMID: 40567697 Free PMC article.
-
Blockchain-Based Trust Management Framework for Cloud Computing-Based Internet of Medical Things (IoMT): A Systematic Review.Comput Intell Neurosci. 2022 May 19;2022:9766844. doi: 10.1155/2022/9766844. eCollection 2022. Comput Intell Neurosci. 2022. Retraction in: Comput Intell Neurosci. 2023 Dec 13;2023:9867976. doi: 10.1155/2023/9867976. PMID: 35634070 Free PMC article. Retracted.
References
-
- Aché M. Cholesterol. Kaggle. 2020. https://www.kaggle.com/datasets/mathurinache/cholesterol. https://www.kaggle.com/datasets/mathurinache/cholesterol (accessed 5 December 2023)
-
- Akkar HA, Salman SA. Cicada swarm optimization: a new method for optimizing persistent problems. International Journal of Intelligent Engineering & Systems. 2020;13(6):279. doi: 10.22266/ijies2020.1231.25. - DOI
-
- Alamer AMA. A secure and privacy blockchain-based data sharing scheme in mobile edge caching system. Expert Systems with Applications. 2023;237:121572. doi: 10.1016/j.eswa.2023.121572. - DOI
-
- Anitha P, Srimathi C. Blockchain based epsilon greedy and hadamard gradient deep secured information sharing for pharma supply chain. International Journal of System Assurance Engineering and Management. 2022;15(1):1–15. doi: 10.1007/s13198-022-01746-7. - DOI
-
- Awadallah R, Samsudin A, Teh JS, Almazrooie M. An integrated architecture for maintaining security in cloud computing based on blockchain. IEEE Access. 2021;9:69513–69526. doi: 10.1109/access.2021.3077123. - DOI
LinkOut - more resources
Full Text Sources
