Federated learning with LSTM for intrusion detection in IoT-based wireless sensor networks: a multi-dataset analysis
- PMID: 40567740
- PMCID: PMC12190250
- DOI: 10.7717/peerj-cs.2751
Federated learning with LSTM for intrusion detection in IoT-based wireless sensor networks: a multi-dataset analysis
Abstract
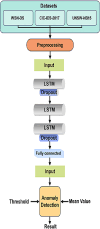
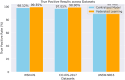
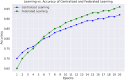
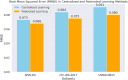
Intrusion detection in Internet of Things (IoT)-based wireless sensor networks (WSNs) is essential due to their widespread use and inherent vulnerability to security breaches. Traditional centralized intrusion detection systems (IDS) face significant challenges in data privacy, computational efficiency, and scalability, particularly in resource-constrained IoT environments. This study aims to create and assess a federated learning (FL) framework that integrates with long short-term memory (LSTM) networks for efficient intrusion detection in IoT-based WSNs. We design the framework to enhance detection accuracy, minimize false positive rates (FPR), and ensure data privacy, while maintaining system scalability. Using an FL approach, multiple IoT nodes collaboratively train a global LSTM model without exchanging raw data, thereby addressing privacy concerns and improving detection capabilities. The proposed model was tested on three widely used datasets: WSN-DS, CIC-IDS-2017, and UNSW-NB15. The evaluation metrics for its performance included accuracy, F1 score, FPR, and root mean square error (RMSE). We evaluated the performance of the FL-based LSTM model against traditional centralized models, finding significant improvements in intrusion detection. The FL-based LSTM model achieved higher accuracy and a lower FPR across all datasets than centralized models. It effectively managed sequential data in WSNs, ensuring data privacy while maintaining competitive performance, particularly in complex attack scenarios. FL and LSTM networks work well together to make a strong way to find intrusions in IoT-based WSNs, which improves both privacy and detection. This study underscores the potential of FL-based systems to address key challenges in IoT security, including data privacy, scalability, and performance, making the proposed framework suitable for real-world IoT applications.
Keywords: Data privacy; Federated learning; Intrusion detection; IoT; LSTM; Real-time detection; Wireless sensor networks.
© 2025 Anwar et al.
Conflict of interest statement
The authors declare that they have no competing interests.
Figures




References
-
- Abuserrieh L, Alalfi MH. A survey on verification of security and safety in IoT systems. IEEE Access. 2024;12(8) doi: 10.1109/ACCESS.2024.3413071. 138627–138645. - DOI
-
- Akyildiz I. Wireless sensor networks: a survey. Computer Networks (Elsevier) 2002;2:6–14. doi: 10.1016/S1389-1286(01)00302-4. - DOI
-
- Almomani I, Al-Kasasbeh B, Al-Akhras M. WSN-DS: a dataset for intrusion detection systems in wireless sensor networks. Journal of Sensors. 2016;2016(1):4731953. doi: 10.1155/2016/4731953. - DOI
-
- Ananthakumar A, Ganediwal T, Kunte A. Intrusion detection system in wireless sensor networks: a review. International Journal of Advanced Computer Science and Applications. 2015;6(12):131–139. doi: 10.14569/issn.2156-5570. - DOI
-
- Anwar RW, Abdullah T. DBTS: distributed blockchain-based trust scheme for data privacy and security in smart cities. Proceedings of the Future Technologies Conference; Cham: Springer; 2023. pp. 415–425.
LinkOut - more resources
Full Text Sources
Miscellaneous
