Blockchain enhanced distributed denial of service detection in IoT using deep learning and evolutionary computation
- PMID: 40593035
- PMCID: PMC12217754
- DOI: 10.1038/s41598-025-06568-8
Blockchain enhanced distributed denial of service detection in IoT using deep learning and evolutionary computation
Abstract
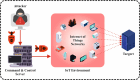
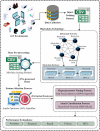
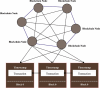
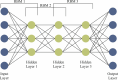
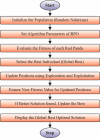
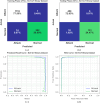
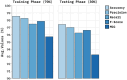
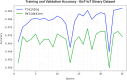
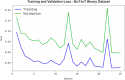
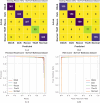
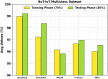
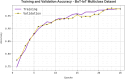
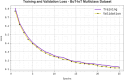
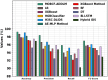
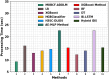
The Internet of Things (IoT) is emerging as a new trend mainly employed in developing numerous vital applications. These applications endure on a federal storage framework primarily concerned with multiple issues. Blockchain technology (BC) is one of the supportive methods for developing IoT-based applications. It is employed to solve the problems encountered in IoT applications. The attack Distributed Denial of Service (DDoS) is one of the leading security attacks in IoT systems. Attackers can effortlessly develop the exposures of IoT gadgets and restrain them as fragments of botnets to commence DDoS threats. The IoT devices are said to be resource-constrained with computing resources and restricted memory. As a developing technology, BC holds the possibility of resolving security problems in IoT. This paper proposes the Metaheuristic-Optimized Blockchain Framework for Attack Detection using a Deep Learning Model (MOBCF-ADDLM) method. The main intention of the MOBCF-ADDLM method is to deliver an effective method for detecting DDoS threats in an IoT environment using advanced techniques. The BC technology is initially applied to mitigate DDoS attacks by presenting decentralized security solutions. Furthermore, data preprocessing utilizes the min-max scaling method to convert input data into a beneficial format. Additionally, feature selection (FS) is performed using the Aquila optimizer (AO) technique to recognize the most relevant features from input data. The attack classification process employs the deep belief network (DBN) technique. Finally, the red panda optimizer (RPO) model modifies the hyper-parameter values of the DBN model optimally and results in higher classification performance. A wide range of experiments with the MOBCF-ADDLM approach is performed under the BoT-IoT Binary and Multiclass datasets. The performance validation of the MOBCF-ADDLM approach portrayed a superior accuracy value of 99.22% over existing models.
Keywords: Blockchain; DDoS attack; Deep learning; IoT; Red panda optimizer.
© 2025. The Author(s).
Conflict of interest statement
Declarations. Competing interests: The authors declare no competing interests. Ethics approval: This article contains no studies with human participants performed by any authors.
Figures


References
-
- Hamouda, D., Ferrag, M. A., Benhamida, N. & Seridi, H. P. P. S. S. A privacy-preserving secure framework using blockchain-enabled federated deep learning for industrial IoTs. Pervasive Mob. Comput.88, 101738 (2022). - DOI
-
- Al-Shammari, N. K., Syed, T. H. & Syed, M. B. An Edge–IoT framework and prototype based on blockchain for smart healthcare applications. Eng. Technol. Appl. Sci. Res.11, 7326–7331 (2021). - DOI
-
- Shah, H. et al. Deep learning-based malicious smart contract and intrusion detection system for IoT environment. Mathematics11, 418 (2023). - DOI
LinkOut - more resources
Full Text Sources

