Integration of metaheuristic based feature selection with ensemble representation learning models for privacy aware cyberattack detection in IoT environments
- PMID: 40595948
- PMCID: PMC12217269
- DOI: 10.1038/s41598-025-05545-5
Integration of metaheuristic based feature selection with ensemble representation learning models for privacy aware cyberattack detection in IoT environments
Abstract
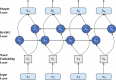
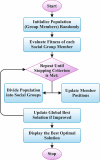
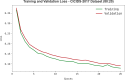
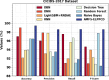
The Internet of Things (IoT) connects virtual and physical objects inserted with software, devices, and other technology that interchange data utilizing the Internet. It enables diverse devices and individuals to exchange data, interconnect, and personalize services to ease usage. Despite IoT's merits, rising cyberthreats and the rapid growth of smart devices increase the risk of data breaches and security attacks. The increasing complexity of cyberattacks demands advanced intrusion detection systems (IDS) to defend crucial assets and data. AI techniques such as machine learning (ML) and deep learning (DL) have shown robust potential in improving IDS performance by accurately detecting and classifying malicious network behavior in IoT environments. This manuscript proposes an Adaptive Metaheuristic-Based Feature Selection with Ensemble Learning Model for Privacy-Preserving Cyberattack Detection (AMFS-ELPPCD) technique. The data normalization stage initially applies Z-score normalization to convert input data into a beneficial format. The AMFS-ELPPCD model utilizes the adaptive Harris hawk optimization (AHHO) model for the feature process selection of the subset. Furthermore, ensemble models such as bidirectional gated recurrent unit (BiGRU), Wasserstein autoencoder (WAE), and deep belief network (DBN) are used for the classification process. Finally, social group optimization (SGO) optimally adjusts the ensemble classifiers' hyperparameter values, resulting in better classification performance. A set of simulations is performed to exhibit the promising results of the AMFS-ELPPCD under dual datasets. The experimental validation of the AMFS-ELPPCD technique portrayed a superior accuracy value of 99.44% and 98.85% under the CICIDS-2017 and NSLKDD datasets over existing models.
Keywords: Cyberattack detection; Data normalization; Ensemble learning model; Feature selection; Social group optimization.
© 2025. The Author(s).
Conflict of interest statement
Declarations. Competing interests: The authors declare no competing interests. Consent to participate: Not applicable. Ethics approval: This article contains no studies with human participants performed by any authors. Informed consent: Not applicable.
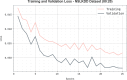
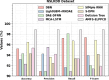
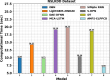
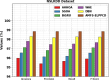
Figures












References
-
- Ahanger, T. A., Ullah, I., Algamdi, S. A. & Tariq, U. Machine learning-inspired intrusion detection system for IoT: Security issues and future challenges. Computers and Electrical Engineering123, 110265 (2025). - DOI
-
- Mishra, S. The impact of AI-based cyber security on the banking and financial sectors. Journal Cybersecur. & Inform. Management, 14(1), 8–19 (2024).
-
- Alghamdi, M. I. An investigation into the effect of cybersecurity on attack prevention strategies. J. Cybersecur. Inform. Manage.3 (2), 53–60 (2020). - DOI
-
- Lee, I. Internet of things (IoT) cybersecurity: literature review and IoT cyber risk management. Future Internet. 12 (9), 157 (2020). - DOI
-
- Albalawi, A. M. & Almaiah, M. A. Assessing and reviewing of cyber-security threats, attacks, mitigation techniques in IoT environment. J. Theor. Appl. Inf. Technol.100, 2988–3011 (2022).
LinkOut - more resources
Full Text Sources

